The stage was set, the players were ready, and Black Hat USA 2023 delivered a cybersecurity spectacle that left no doubt—this was a game-changing event. As we unpack the highlights, one overarching theme emerges: a united front against ever-evolving threats. From generative AI to cloud security and a glimpse into the future of defense, this year's conference illuminated the power of collaboration and innovation. Amidst these pivotal discussions, one revelation—the TETRA:BURST vulnerabilities—took center stage, leaving an indelible mark on the field.
Generative AI – Powering Defense with Intelligence
Picture this: cybersecurity professionals stepping onto the field as a united front, equipped with generative AI—a strategic powerhouse. This technology showcased its mettle in rewriting the rulebook of threat detection and response. Just as a seasoned quarterback analyzes the defense and calls the shots, generative AI intercepted potential threats and neutralized them before they could advance. Black Hat 2023 ignited with sessions demonstrating how this tool is shaping the future of cybersecurity, proving that intelligence-driven defense is a game-changer.
Cloud Security – Fortifying the Digital Citadel
In the digital arena, the cloud acted as a playing field that demanded unyielding defense. The discussions at Black Hat revolved around shoring up cloud security. From managing posture to executing vulnerability scans, the playbook was thorough. Black Hat's stage saw experts discussing strategies that ensured the safety of digital assets, and their defenses were ready to field any threats that came their way. Penetration testing, offensive security, cryptography, and forensics were also high on the list of topics, providing a diverse skillset for players in this never-ending cybersecurity game.

Chart: Top 10 Black Hat 2023 training topics, data compiled by Google Bard
The Future's Blueprint – Charting a Collective Path
Peering into the future, the spotlight is on innovation. With the opposition continuously refining their plays, the home team countered with a roster of emerging technologies—AI, machine learning, and cloud security. These technologies stood ready to rewrite the rules of engagement, predicting and preventing threats before they could take hold. Black Hat 2023 painted a vivid picture of a united front against evolving adversaries, signaling that a new era of defense is on the horizon. The keynotes were especially insightful with focus on AI, state actors, and the new National Cybersecurity Strategy Plan released by the White House.
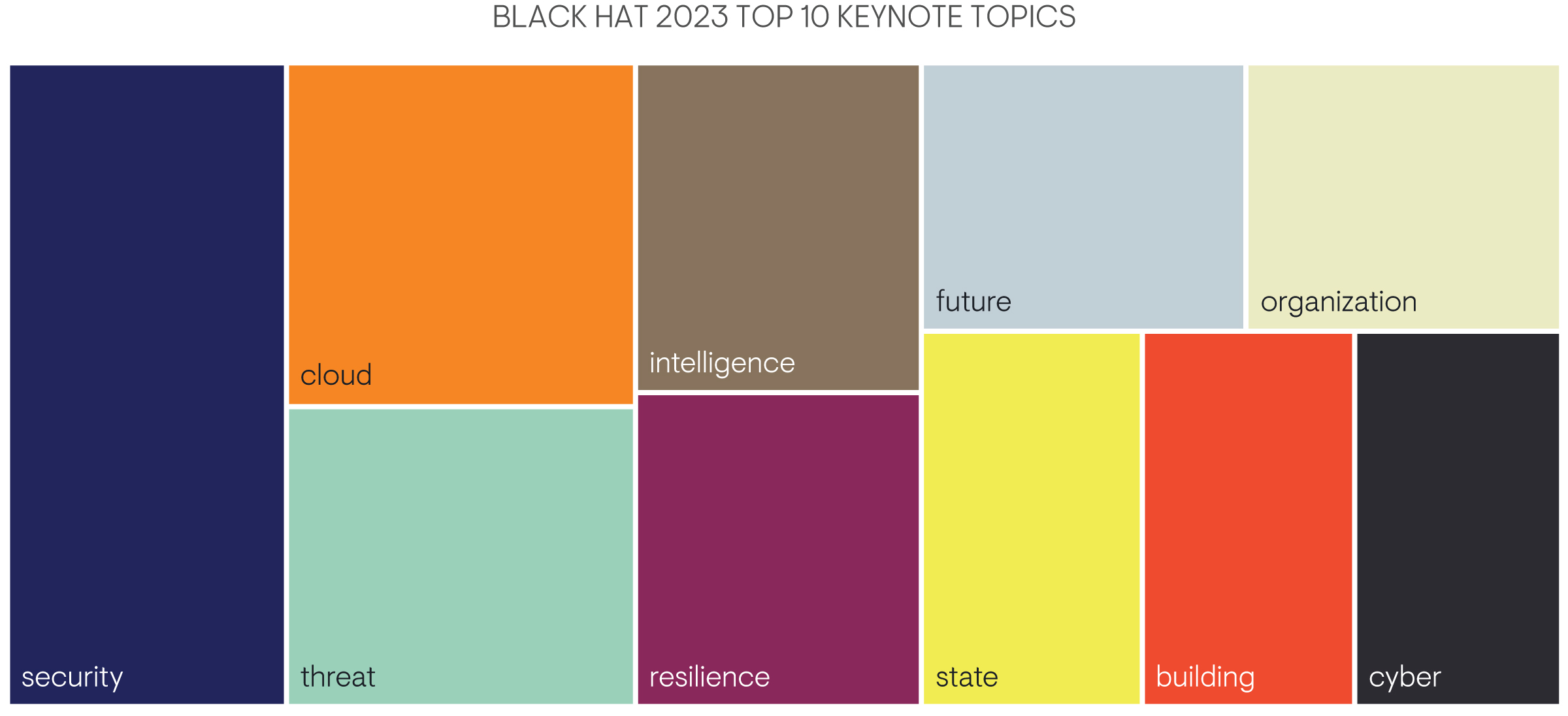
Chart: Top 10 Black Hat 2023 Keynote Topics, data compiled by Google Bard
Collaboration Beyond the Field – The Cyber Community's Role
Beyond the vendors and the presentations, the true essence of Black Hat 2023 was collaboration. Just as a championship team relies on each player's unique strengths, the cybersecurity community emphasized unity. From public to private sectors, the message was clear: working together amplifies the impact. This collaborative spirit was exemplified when the TETRA:BURST vulnerabilities were revealed, showcasing vulnerabilities that transcend individual domains and demand a collective defense strategy.
I had a lot of very interesting conversations at Black Hat, including conversations regarding how we need to be cautious with generative AI because there are still a lot of security concerns. In fact, representatives from BlackBerry informed me their own research showed that 75% of IT decision-makers currently want to ban ChatGPT in their organizations. Other vendors are working to embrace generative AI safely, with unique use cases such as using AI to convert natural language queries into tool-specific queries, or using AI as a virtual assistant to help configure their platforms. Outside of the AI conversations, I also had the privilege of discussing with CISO Global how cybersecurity is a team sport, and there’s a need for more vendors to collaborate with each other, even if they’re competitors.
TETRA:BURST – The Unforeseen Challenge
Amidst the broader themes, the revelation of TETRA:BURST vulnerabilities was an unexpected twist. A collection of vulnerabilities affecting the Terrestrial Trunked Radio (TETRA) standard, TETRA:BURST's impact was felt across sectors. With two of the vulnerabilities classified as critical, the stakes were high. These vulnerabilities exposed potential security challenges for law enforcement, military, critical infrastructure, and more. The weaknesses ranged from real-time decryption to session key pinning, demanding immediate action and strategic adaptation from cybersecurity professionals. The most important takeaway? Security through obscurity isn’t security, and if you need to make encryption algorithms secret, they probably aren’t that secure in the first place.
A Gameplay of Strategy – Key Takeaways
All in all, the Black Hat USA 2023 conference was a touchdown. Generative AI, cloud security, and a vision of the future showcased an industry poised to defend with intelligence, resilience, and innovation. The TETRA:BURST vulnerabilities reinforced the urgency of collaboration and adaptability. Just as in any complex game, the players—ranging from AI algorithms to cloud architects—exemplified the true spirit of cybersecurity: a relentless pursuit of safety, unity, and the promise of a safer digital future. As my new friends at CISO Global would say, cybersecurity is a team sport. Let’s play ball, and work together toward a safer tomorrow.
EMA is currently seeking sponsors for our upcoming artificial intelligence-focused research project. If this is of interest to your organization, please contact us.




