Organizations are constantly dealing with rapid shifts toward cloud computing, escalating security threats, and regulatory frameworks that have necessitated more robust solutions in data governance. As they continue to accumulate more and more sensitive data, the need for visibility into data assets becomes obvious. Moreover, regulations such as GDPR, HIPAA, ITAR, and PCI impose stringent compliance requirements, compelling organizations to ensure that they can not only manage, but also protect, their data effectively.
BigID Unveils BigID Next
By Chris Steffen on Feb 24, 2025 8:29:53 AM
RSAC 2022 Closing Thoughts - Return of Cybersecurity Conferences to the Wild, Wild West Coast
By Ken Buckler on Jun 16, 2022 9:43:34 AM
It’s time to circle the wagons and defend the data and users
As the world reopens, the conference booths light with excitement and empty expo halls are once again filled with hustle and bustle. I thought it important to take a moment and look at what changed in the past two years and where the security industry has room for improvement. This was the first in-person RSA Conference, and likely the first major security conference at all for that matter, with large in-person attendance after the peak of the COVID-19 pandemic. While the conference looks very similar to conferences before the pandemic, the cybersecurity industry landscape has drastically changed.
The Top 5 IoT Lessons I Learned From Hollywood
By David Monahan on Sep 23, 2016 12:07:46 PM
In my last IoT blog, I talked about the history of IoT and the evolution of issues surrounding IoT devices. In this part of the series, we will expand on the issues around IoT and the data it collects.
Endpoint Management and Security – More Effective as Partners than Adversaries
By Steve Brasen on Sep 2, 2016 10:59:52 AM
The primary function of enterprise IT management is to empower end users with access to technology resources that will boost their productivity and job performance. However, this focus is at odds with the core precepts of IT security which are adopted to minimize the exposure of enterprise systems, applications, and data. I recall that in a number of IT operations management adventures throughout my career, I often joked with colleagues that the most effective way to create a secure environment is to simply shut down all computers in the data center. Naturally, management executives dependent on the IT infrastructure to generate revenue were not amused by my flippancy…and even less happy that their workers had to “jump through hoops” to gain access to IT resources.
Effective Security Requires a Change in Mindset and the Protection Paradigm
By David Monahan on Aug 24, 2016 11:05:53 AM
Nearly every day another successful breach is reported. In 2016 alone, organizations from major governmental agencies such as the IRS and Department of Defense, to major retailers including Wendy’s, have succumbed to attack. These organizations are not alone; every major business and governmental sector has been compromised. Large tech companies such as LinkedIn and Oracle, healthcare providers including Premier Healthcare (as well as numerous hospitals), manufacturers, major educational institutions, and large financial organizations have all succumbed to either internal or external threats.
The Desperate Need for Accuracy and Efficiency in Security for Detecting Network Intruders and Other Threat Actors Quickly
By David Monahan on Apr 14, 2016 2:37:49 PM
According to 2015 research reports published by Ponemon, Mandiant, and others, median intruder dwell time in a target network prior to detection ranges from just under to just over 200 days. That is a little over six months and as everyone agrees, totally unacceptable.
HEAT Software Meets the Need for Endpoint Protection Head-On
By David Monahan on Dec 11, 2015 12:40:49 PM
In many organizations, endpoints see virtually constant change. Users access, download, and utilize applications, data, drivers, files, toolbars, widgets, etc., introducing both new security threats and undocumented changes in systems and processes. For better or for worse, all of these activities leave their mark on the endpoint.
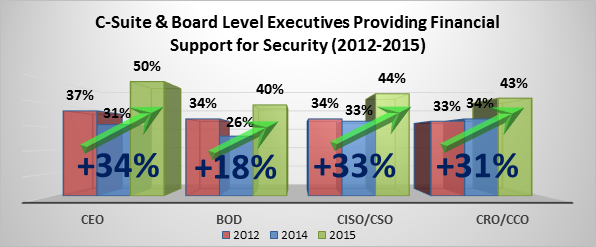
EMA Research Shows that Cyber Security is Achieving Executive Visibility in a Big Way
By David Monahan on Nov 20, 2015 12:50:32 PM
One of the services that EMA provides to the tech industry is research. During the course of the year, numerous projects are launched to help IT consumers and vendors understand market perceptions. EMA then provides analysis and forecasts on trends based upon those perceptions.
The Limits of Packet Capture
By David Monahan on Aug 19, 2015 3:42:12 PM
In preparation for my new ‘Achieving Hi-Fidelity Security’ research project, I thought I would post a relevant blog I wrote for InformationSecurityBuzz.com.
Vectra Provides Pervasive Visibility & Analysis to Detect Cyber Attacks
By David Monahan on Apr 9, 2015 2:21:39 PM
Though cyber attacks have been around for years, in 2014 there was an explosion in the volume of attacks and a marked increase in the losses and damages they inflicted. In 2015, this does not seem to be lightening up.