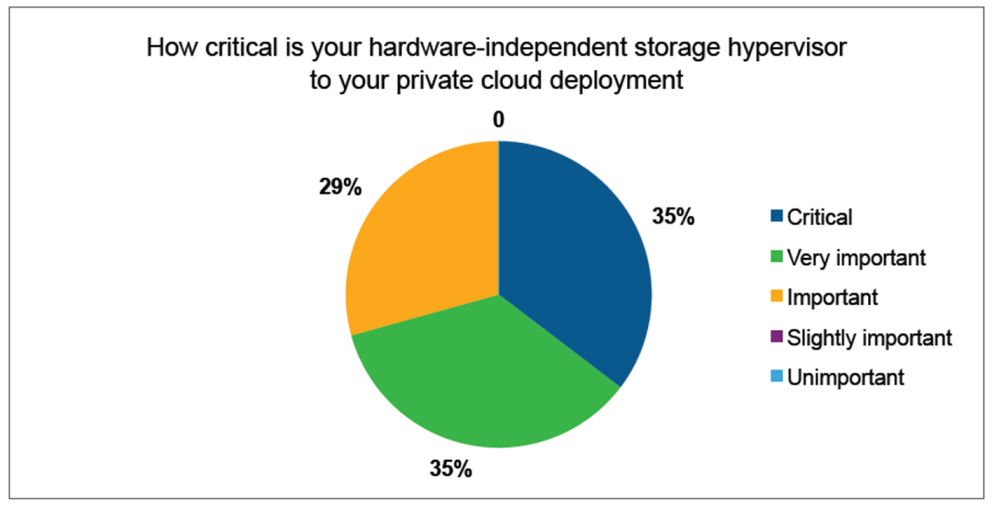
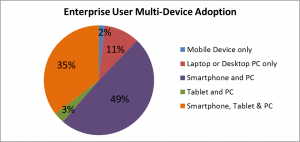
The Havana release of OpenStack was launched on October 17, about three weeks prior to the OpenStack Summit in Hong Kong. As always, there are many new features -high availability, load balancing, easier upgrades, plugins for development tools, improved SDN support, fiber channel SAN support, improved bare metal capabilities- and even two new core components, Ceilometer -metering and monitoring- and Heat -orchestration of the creation of entire application environments- to admire. Without any doubt, OpenStack is becoming more enterprise ready with each new release .
Rapid Evolution – OpenStack Is Growing Up
By Torsten Volk on Oct 28, 2013 9:21:05 AM
War of the Stacks: OpenStack vs. CloudStack vs. vCloud vs. Amazon EC2
By Torsten Volk on Oct 14, 2013 2:25:19 PM
When it comes to cloud technologies, discussions often get passionate or even heated. It’s all about the “war of the stacks”, where much Cool Aid is dispensed to get customers to buy into the respective cult. This discussion reminds me of the old days of enterprise IT, where everything was about technology instead of business value. You either bought one thing or the other and then you were locked in for a half decade. Dark times.
VMworld 2013 Digest – 8 Companies You Should Take a Closer Look At
By Torsten Volk on Sep 3, 2013 12:02:14 PM
Every year after VMworld EMA receives countless inquiries regarding the most notable vendors on the show floor. This time around, we have compiled a list consisting of startups taking a new look at traditional IT challenges, as well as larger and more mature companies that have launched industry transforming initiatives. Ultimately, this list of eight extraordinary vendors is focused on one central concept: customer value.
The Impact of Cloud on Data Protection: Ripple or Sharknado™
By Torsten Volk on Aug 14, 2013 12:35:47 PM
It’s always like that in enterprise IT. There’s this incredible new technology that lets you do things you could never even fathom possible. But then, once the honeymoon is over, the old problems come back to bite you with a vengeance.
Review of the Microsoft SURFACE RT – A Story of What Could Have Been
By Torsten Volk on Jul 18, 2013 7:22:11 PM
Now that I have spent a month with my latest gadget, a Microsoft Surface RT, I want to share some thoughts on the device, as well as on Windows 8. I have been a happy iPad user for the previous 2 years, but have sorely missed MS Office on this excellent device. As much as I like -if not love- the iPad, there was this key moment on a flight to Boston that made me wonder if there’s not a better tablet out there for doing my work. The casualty was a 28 page research report, with plenty of charts and tables. I used QuickOffice, a highly rated productivity suite for iPad, to complete a final edit of my document. To make it short, after 3 hours of editing, the document was damaged beyond repair, even by the EMA production team, and I ended up with the infuriating manual task of having to open up a previous version of my doc on one and the entirely garbled version on another screen and manually restore my edits. Not fun.
OpenStack Thoughts – Part 2: Impact on VMware
By Torsten Volk on Jun 20, 2013 9:56:22 AM
At EMA, we constantly receive inquiries regarding what OpenStack means to the VMware portfolio. Is it a competing technology? Are OpenStack and vCloud complementary? Why did VMware join OpenStack? What are the typical use cases for OpenStack as opposed to vCloud? To address these questions, let’s take a step back and take a look at what OpenStack is and, as importantly, what it is not. This post is building on my previous article on the business value of OpenStack.
Maybe We Should Call It The “Pre-Post-PC” Era?
By Steve Brasen on Jun 6, 2013 9:48:41 AM
IT marketing hype has generated quite a few ridiculous and sometimes outright bizarre phrases to describe trends in technology adoption, but few on the list of the absurd top the insistence that we live in a “post-PC” era. The concept of “post-PC” derives from the (correct) fact that mobile device adoption has broadly accelerated, but makes the incorrect assumption that this is causing a substantial decrease in PC use. Nothing could be further from the truth – especially in relation to the business use of desktop and laptop PCs.
Dell’s Clean Slate Approach to Enterprise IT
By Torsten Volk on May 8, 2013 7:22:09 PM
Breaking News: Dell Acquires Enstratius to Further Complete Its Cloud Story
OpenStack Thoughts – Part 1: Key Business Considerations
By Torsten Volk on Apr 22, 2013 10:27:18 AM
OpenStack’s huge momentum is undeniable. IBM, RedHat, NetApp, Rackspace, HP, Dell, Cisco, Intel and even VMware have committed significant funds and human resources to this project. But why would companies, that are otherwise competing rather fiercely, sit on one table to build an OpenSource cloud platform?
The Software Defined Datacenter: Part 4 of 4 – Where We Are Today
By Torsten Volk on Mar 26, 2013 3:58:50 PM
Almost one year into the discussion about the Software Defined Data Center (SDDC), it is time to take inventory of the state of the discipline. As a reminder, the ultimate goal of the SDDC is to abstract and centralize the
management of compute, network, storage, operating systems, middleware and applications in order to dynamically place workloads where they can run in the most cost efficient, secure and compliant manner.