Network operations teams are increasingly seeking AI tools to improve their ability to build and manage infrastructure. In fact, they now expect AI features and products from their network infrastructure and network management vendors.
A Path Toward Trusting Agentic NetOps
By Shamus McGillicuddy on Mar 4, 2026 11:11:58 AM
The Great Device Reset: Mapping the 2025 Management Landscape, the Linux Management Blind Spot, and the 2026 Shift
By Ken Buckler on Feb 2, 2026 11:43:55 AM
In early 2026, the world of IT fleet management is undergoing its most radical transformation since the 2020 remote work pivot. The original intent of device management solutions was to make managing multiple computers that required the same configuration easier. Today, it has become the frontline of corporate survival.
A Scammer Sent Me His Source Code? A Cautionary Tale of the Dangers of Vibe Coding
By Ken Buckler on Jan 27, 2026 10:10:03 AM
Late last night, Mr. William Chalmers from Lloyds Banking Group in the United Kingdom sent me quite an unusual email. With the subject “Mutual Investment,” I absolutely expected yet another boring investment scam email which would promptly go into the spam bin. However, upon opening this email I was pleasantly surprised to see that this scammer had not sent me an “investment opportunity” (read that as investment scam) but accidentally emailed me his source code. Oops. I won’t include the full code here, but I will include some interesting snippets.
The "Triple Threat" of 2026: Why Your AI Workforce Is Your Biggest Security Blind Spot
By Ken Buckler on Jan 19, 2026 3:55:52 PM
If 2025 was the year the industry aggressively deployed agentic AI to automate everything from code deployment to customer service, 2026 is shaping up to be the year we pay the security debt for that speed. We have effectively built an "AI-native" enterprise ecosystem, but in doing so, we have introduced a new class of insider threat that doesn't sleep, doesn't take breaks, and crucially doesn't think like a human.
EMA at 30: The Value of Consistency
By Shamus McGillicuddy on Jan 16, 2026 12:40:17 PM
EMA turns 30 this year. We're not the largest analyst firm, and we’re not the loudest. What we have always strived to be is honest, independent, and reliable.
A Banner Year: Highlighting EMA's 2025 Network Infrastructure and Operations Research
By Shamus McGillicuddy on Jan 9, 2026 8:37:59 AM
The network infrastructure and operations industry is on fire. How do I know? Just look at how busy the Network Infrastructure and Operations practice at Enterprise Management Associates (EMA) was in 2025.
Cybersecurity Trends to Consider in 2026
By Chris Steffen on Jan 2, 2026 12:33:48 PM
As I sit here watching the very soggy Rose Parade, my thoughts drift to the cybersecurity topics and trends we will talk about in 2026 (yes, that is how much of a nerd I actually am).
Is 2026 the Year we Finally Master Zero Trust? Or the Year of Agentic Data Breaches?
By Ken Buckler on Dec 23, 2025 11:14:28 AM
Well, 2025 has been an extremely interesting year with what can only be described as a massive explosion of agentic AI. And while agentic might hold a large amount of potential to address deficiencies the industry has struggled with for years, with great power comes great responsibility.
ServiceOps is the Right Idea. So why is it Such a Challenge?
By Parker Hathcock on Dec 11, 2025 4:25:35 PM
IT professionals don’t need to be convinced that silos are a problem. Most of us have lived that reality: the service desk doesn’t have visibility into operations, operations teams aren’t looped in on service priorities, and tickets, alerts, and metrics are disconnected and delayed. Everyone works hard, often heroically, but coordination is reactive, and the gaps show up in ways that users and the business always notice.
Getting Started with a Network Source of Truth
By Shamus McGillicuddy on Dec 8, 2025 12:37:46 PM
A growing number of network engineering teams are adopting network source of truth tools. What are they? And how should you go about setting one up? Enterprise Management Associates (EMA) has published new research on this subject that answers these questions. For this research, EMA analysts conducted long-form interviews with 17 network engineers about their approaches to establishing and maintaining a network source of truth.
Five Things I'm Thankful for in Cybersecurity This Thanksgiving
By Chris Steffen on Nov 26, 2025 5:30:04 PM
Happy Thanksgiving, everyone!
Cybersecurity Awesomeness Podcast Recap – Episode 134: LLM Prompt Injection Attacks
By Chris Steffen & Ken Buckler on Nov 17, 2025 8:17:44 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, vice president of research, and Ken Buckler, research director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laid-back podcast is for listeners of all skill levels and backgrounds.
The OpenAI Dealbook: The trillion-dollar compute economy
By Chris Steffen on Nov 4, 2025 9:35:20 AM
If you’ve tried to track the blizzard of OpenAI partnership announcements lately, you might feel like you’re watching the most ambitious infrastructure strategy ever conceived, or a Three Stooges-style routine where everyone keeps paying the same $20 back and forth…except now it’s $20 billion.
Why Technology Resiliency Isn't Optional Anymore
By Chris Steffen on Oct 21, 2025 12:22:40 PM
The recent news brings to light a topic that is top of mind in my research and studies lately: technology resiliency.
Cybersecurity Awesomeness Podcast Recap - Episode 129: Data Security and Software Updates
By Chris Steffen & Ken Buckler on Oct 17, 2025 9:06:33 AM
Cybersecurity Awesomeness Podcast – It’s 2025. Do You Know Where Your Data is?
Welcome to the recap of the Enterprise Management Associates (EMA™) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, vice president of research, and Ken Buckler, research director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
The Cybersecurity Impacts of the Nobel Prize
By Chris Steffen on Oct 13, 2025 9:40:16 AM
The Nobel Committee has spoken, and for those of us living in the bright lights of the cybersecurity world, it is a day of celebration. The 2025 Physics Prize, awarded to John Clarke, Michel H. Devoret, and John M. Martinis for their work on "macroscopic quantum mechanical tunnelling and energy quantisation," isn't just a headline; it is a validation of the potential of the Quantum Age.
Cybersecurity & Marketing in the Wake of Google's September Data Disruption
By Chris Steffen on Oct 8, 2025 10:43:06 AM
The world of digital marketing thrives on data, and for years, Google Search Console (GSC) and third-party SEO tools have been our compass. But as an industry analyst, I can tell you that the past few weeks have felt like driving a car without windows! What initially appeared as inexplicable fluctuations in our SEO dashboards has coalesced into a clear, albeit unsettling, picture: Google quietly pulled the plug on a foundational data-gathering mechanism, unleashing a wave of disruption that impacts everyone from enterprise marketers to cybersecurity businesses.
Google’s New Android Developer Verification Will Increase Device Security Risk for Power Users
By Ken Buckler on Oct 6, 2025 12:10:49 PM
Google's upcoming Android Developer Verification Program (ADVP), which launches fully in 2026, requires all developers to register and verify their identities before their applications can be installed on certified Android devices.
Focusing on the Five Most Critical Cybersecurity Shifts by 2026
By Chris Steffen on Oct 3, 2025 11:57:22 AM
The digital threat landscape is accelerating, making it critical for security leaders to prioritize the most impactful shifts. Instead of trying to tackle every emerging threat, focus your strategy and budget on these five essential cybersecurity trends that will dominate 2026, forcing a fundamental change in how your organization protects its assets.
With What Snack Food Will You Authenticate? Identity Week 2025
By Ken Buckler on Sep 19, 2025 11:28:32 AM
When I attended the Identity Week conference in Washington, D.C. last year, I noted a heavy focus on biometrics, especially focused on employee onboarding and background checks. While this is an important topic, I was disappointed that there wasn’t more focus on identity security and non-human identities. This year at Identity Week, that changed significantly.
Cybersecurity Awesomeness Podcast Recap - Episode 123: Cybersecurity and the New School Year
By Chris Steffen & Ken Buckler on Sep 18, 2025 7:31:05 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 122: Proactive vs. Reactive Cybersecurity
By Chris Steffen & Ken Buckler on Sep 17, 2025 9:46:02 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Black Hat 2025: The Year of the AI Arms Race
By Chris Steffen on Aug 15, 2025 11:54:07 AM
The recent conclusion of Black Hat USA 2025, which saw over 20,000 security professionals converge in Las Vegas, served as a powerful barometer for the state of the cybersecurity industry. The event, with its more than 100 briefings and 115 in-person tool demos, underscored the continued evolution of the threat landscape. The conversations in the business hall and around the conference revealed a cybersecurity world trying to grapple with new forms of risk, a shifting vendor landscape, and an ever-expanding attack surface that now extends to every corner of our digital lives.
Cybersecurity Awesomeness Podcast Recap - Episode 118: Zero Day Attack on SharePoint
By Chris Steffen & Ken Buckler on Jul 28, 2025 9:19:48 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 117: The Security Triad
By Chris Steffen & Ken Buckler on Jul 23, 2025 9:31:02 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 116: False Sense of Cybersecurity
By Chris Steffen & Ken Buckler on Jul 14, 2025 9:16:00 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 115: The Clickbait News Cycle
By Chris Steffen & Ken Buckler on Jul 7, 2025 12:39:35 PM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 114: Nation State Cyber Attacks
By Chris Steffen & Ken Buckler on Jun 30, 2025 12:10:49 PM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
What the Iran conflict means for the cybersecurity industry
By Ken Buckler on Jun 24, 2025 11:45:30 AM
The recent U.S. strikes on Iranian nuclear facilities dramatically reshaped the cyberthreat landscape facing American networks. In the weeks and possibly even months following the bombings, cybersecurity professionals should anticipate a surge in both opportunistic and state-aligned intrusions aimed at disrupting critical systems, stealing sensitive data, or undermining public confidence in digital infrastructure. Understanding the motivations, tactics, and potential targets of these adversaries is essential for organizations seeking to bolster their defenses and maintain operational resilience.
Cybersecurity Awesomeness Podcast Recap - Episode 113: On Premise vs. Cloud vs. SaaS
By Chris Steffen & Ken Buckler on Jun 23, 2025 8:48:17 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 112: Penetration Testing
By Chris Steffen & Ken Buckler on Jun 12, 2025 12:59:50 PM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 110: Supply Chain Attacks
By Chris Steffen & Ken Buckler on May 27, 2025 11:44:23 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 109: Using AI for Cyberattacks
By Chris Steffen & Ken Buckler on May 20, 2025 9:16:30 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 108: RSAC Recap
By Chris Steffen & Ken Buckler on May 12, 2025 11:38:49 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Hack to the Future: AI, Cars, and Quantum Shenanigans at Black Hat Asia 2025
By Ken Buckler on Apr 14, 2025 4:18:52 PM
Black Hat Asia 2025 returned to Singapore with a dynamic mix of technical depth, real-world impact, and plenty of sobering insights about the evolving cybersecurity landscape. Across two packed days, experts from around the globe tackled threats old and new, offering live demonstrations, original research, and thought-provoking commentary on the increasingly blurred lines between digital, physical, and even quantum attack surfaces.
Cybersecurity Awesomeness Podcast Recap - Episode 105: Hacking a Computer-Controlled Vehicle
By Chris Steffen & Ken Buckler on Apr 14, 2025 4:15:57 PM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 104: Taxes and Tariffs
By Chris Steffen & Ken Buckler on Apr 7, 2025 2:51:52 PM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Messaging in Government: Signal, Microsoft Teams, and the Security-Convenience Paradox
By Ken Buckler on Mar 27, 2025 9:45:33 AM
In an era when government operations increasingly rely on digital infrastructure to remain effective, accountable, and secure, messaging platforms emerged as both an enabler and a risk vector. The question of how government agencies communicate—internally, externally, and across jurisdictional lines—is no longer merely a matter of workflow optimization. It is a fundamental aspect of mission assurance, public trust, and operational integrity. Yet even as messaging tools proliferate and mature, the gulf between platforms built for accountability and those designed for privacy remains pronounced. Nowhere is that divide more evident than in the ongoing tension between Microsoft Teams and Signal—two platforms that, while often deployed in parallel, represent fundamentally different answers to the same set of urgent questions about security, control, and digital sovereignty.
Cybersecurity Awesomeness Podcast Recap - Episode 102: Insider Threats
By Chris Steffen & Ken Buckler on Mar 24, 2025 12:17:40 PM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Redefining PTaaS: A Goal-Oriented Approach to Include Bug Bounty Programs
By Ken Buckler on Mar 18, 2025 9:53:47 AM
In an era when cybersecurity threats continue to evolve at an unprecedented pace, organizations are seeking robust, goal-oriented solutions to identify and remediate security vulnerabilities effectively. Traditionally, penetration testing as a service (PTaaS) played a critical role in structured, systematic security assessments. However, as the industry shifts toward more dynamic and continuous testing models, it is becoming increasingly clear that PTaaS needs a redefinition—one that includes the advantages of bug bounty programs under its umbrella.
Cybersecurity Awesomeness Podcast Recap - Episode 101: Tax Scams
By Chris Steffen & Ken Buckler on Mar 14, 2025 9:58:50 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap - Episode 100: UK iPhone Privacy Issues
By Chris Steffen & Ken Buckler on Mar 11, 2025 9:36:03 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap: Episode 99: Marketing Technical Products
By Chris Steffen & Ken Buckler on Feb 27, 2025 11:16:02 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
BigID Unveils BigID Next
By Chris Steffen on Feb 24, 2025 8:29:53 AM
Organizations are constantly dealing with rapid shifts toward cloud computing, escalating security threats, and regulatory frameworks that have necessitated more robust solutions in data governance. As they continue to accumulate more and more sensitive data, the need for visibility into data assets becomes obvious. Moreover, regulations such as GDPR, HIPAA, ITAR, and PCI impose stringent compliance requirements, compelling organizations to ensure that they can not only manage, but also protect, their data effectively.
Cybersecurity Awesomeness Podcast Recap: Episode 98: DDoS Mitigation
By Chris Steffen & Ken Buckler on Feb 21, 2025 8:57:09 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap: Episode 97
By Chris Steffen & Ken Buckler on Feb 14, 2025 11:21:14 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap: Episode 96
By Chris Steffen & Ken Buckler on Feb 11, 2025 9:35:07 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap: Episode 95
By Chris Steffen & Ken Buckler on Feb 5, 2025 2:12:55 PM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap: Episode 94
By Chris Steffen & Ken Buckler on Jan 24, 2025 10:11:58 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap: Episode 93
By Chris Steffen on Jan 17, 2025 10:55:57 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Cybersecurity Awesomeness Podcast Recap: Episode 92
By Chris Steffen & Ken Buckler on Jan 13, 2025 8:41:36 AM
Welcome to the recap of the Enterprise Management Associates (EMA) Cybersecurity Awesomeness (CSA) Podcast. Hosted by Chris Steffen, Vice President of Research and Ken Buckler, Research Director at EMA, the CSA Podcast covers a wide range of cybersecurity topics, from cyber workforce talent shortages to cyber threat intelligence, to current events in technology and security. This short, laidback podcast is for listeners of all skill levels and backgrounds.
Identity Supply Chain – A New Approach to Identity Management and Security
By Ken Buckler on Jan 6, 2025 8:27:01 AM
In today’s interconnected digital landscape, identity has become the cornerstone of both organizational security and user experience. Whether onboarding a new employee or granting a customer access to services, the journey of identity—commonly referred to as the identity supply chain—encompasses a series of critical stages, from initial verification to continuous authentication and authorization.
Cybersecurity in 2025: Trends and Predictions from Industry Experts
By Chris Steffen & Ken Buckler on Dec 20, 2024 12:46:06 PM
The future of cybersecurity is a hot topic, and Episode 91 of the Cybersecurity Awesomeness Podcast dives deep into what 2025 might hold. Hosted by Chris Steffen and Ken Buckler, this episode offers insights into emerging threats, groundbreaking technologies, and the ever-critical human element in security. Here’s what you need to know.
Taking Flight: Aviator Soars One Year in at OpenText World 2024
By Ken Buckler on Dec 6, 2024 9:12:29 AM
OpenText World 2024 highlighted the growing role of AI in enterprise transformation, with Aviator, OpenText’s AI platform, as a focal point. Now one year into its deployment, Aviator has demonstrated significant potential in addressing challenges across industries by integrating AI into business processes. The platform reflects OpenText’s broader strategy of “Elevating Human Potential,” focusing on AI, cloud, and security as key drivers of innovation. Aviator’s emphasis on secure, data-driven AI models has positioned it as a useful tool for tackling the complexity of modern information management.
Bio-whatrics? In the Identity Market, Biometrics Solutions are Gaining Traction, but With Too Narrow a Focus
By Ken Buckler on Sep 17, 2024 9:46:36 AM
I recently had the opportunity to attend Identity Week in Washington, D.C. While this is a smaller conference compared to RSA Conference or Black Hat, some of the conversations were just as powerful and much more focused on the identity market. I was at first encouraged by the large focus of biometrics at the conference, but quickly discouraged upon seeing the limited use cases many of the vendors were promoting.
Avoid These Mistakes When Applying Generative AI to IT Operations
By Shamus McGillicuddy on Sep 12, 2024 3:15:09 PM
Generative AI hype has permeated the world of IT operations. My latest research found that 96% of IT pros who have evaluated or used generative AI for IT management use cases believe it can make people in their organizations more productive.
NaaS Providers Must Offer Observability of Their Networks
By Shamus McGillicuddy on Aug 12, 2024 2:04:07 PM
Network as a service (NaaS) is a class of network infrastructure solutions that are delivered via a cloud-consumption model. Often, these networks are managed offerings, where the provider takes ownership of implementation and day-to-day operations. While a NaaS provider is capable of taking over network management for a customer, many IT organizations prefer to maintain some control and ownership of day-to-day operations for a NaaS-based network.
Review of the 2024 Splunk Conference (or – is Cisco going to mess up Splunk)
By Chris Steffen on Jun 18, 2024 10:56:19 AM
Fresh off a week at the Splunk conference (called .conf24), I want to share a few insights about my time at the show.
Cisco Live: What's the Signal in the AI Noise?
By Shamus McGillicuddy on Jun 4, 2024 3:33:33 PM
Cisco Live is happening in Las Vegas this week. It remains one of the biggest annual gatherings of network infrastructure professionals in the world. It is also a venue for Cisco to showcase its latest products and services, and it is a place where Cisco lays out its overall vision to address customer requirements.
RSA Conference Recap
By Chris Steffen on May 21, 2024 8:56:01 AM
Another RSA conference (not RSA, not #RSA, but “THE RSA Conference” – those that bought the conference do not want it to be associated with RSA the company, which leads me to wonder why they didn’t just rename the thing to something else more securityish) is in the books, and I thought I would share a few thoughts about things I saw and vendors that I met with at the conference.
RSA Conference 2024 Tales from the Show Floor: How Security Needs to Focus on User Experience
By Ken Buckler on May 21, 2024 8:54:09 AM
According to the RSA Conference website, there was a total of 641 vendors exhibiting or sponsoring the conference in the over 738,000 square feet of exhibit space dedicated within the two-million-square-foot Moscone Center. I had meetings scheduled with approximately 20 of these vendors and met with a small handful of additional vendors on the expo floor as time permitted. I didn’t keep track of how far I walked this year, but the entire Moscone Center complex is approximately 87 acres in size. For comparison, the United States Capitol building is only 4 acres. I made several laps around the expo floor each day, as well as walking around the entire complex throughout various parts of the day. Needless to say, my feet are quite tired, but with the conversations I had with vendors, it was worth it.
NetOps Teams Consolidate Tools, But Sprawl Persists
By Shamus McGillicuddy on May 14, 2024 3:16:38 PM
IT organizations have always relied on multiple tools to manage and monitor their networks. This reality is a legacy of the evolution of network management tools. Initially, vendors offered point products that solved very narrow sets of tool use cases like device discovery, device metric collection, config management, traffic monitoring, and so on. Network engineers needed a sprawling toolset to address all aspects of operations.
Using Google Gemini to Analyze Trends in the RSA Conference 2024
By Ken Buckler on May 3, 2024 8:01:10 AM
The RSA Conference 2024 is upon us, and this year promises to be a treasure trove of insights for security professionals. We're particularly excited to explore the latest advancements in areas like AI-powered security and cloud protection. To enhance our analysis, we're putting Google Gemini, a large language model, to the test. Can it navigate the vast amount of information available about the conference and identify the themes that matter most? In this blog, we’ll explore the conference through the lens of Google Gemini, offering previews of sponsor briefings, session topics, and emerging trends that will shape the future of cybersecurity, and we’ll also examine Gemini’s ability to analyze text data.
Network Automation Strategies Must Include Change Validation
By Shamus McGillicuddy on Apr 10, 2024 2:59:02 PM
For most IT organizations, network automation boils down to change management. Network engineering teams implement tools that automate their processes for all manner of changes, including network software patches and upgrades, configuration changes, and security policy updates.
Is Triggered or “Smart” Packet Capture a Foolproof Alternative to Always-On PCAP?
By Shamus McGillicuddy on Mar 22, 2024 11:20:26 AM
To offer more affordable and compact solutions, some solution providers are pitching triggered or “smart” packet capture solutions as an alternative to always-on capture.
Passwords: An Outdated Security Measure in Modern Times
By Ken Buckler on Mar 22, 2024 10:33:03 AM
In an era rampant with cyber threats, the security of passwords and identity remains a critical concern. According to HaveIBeenPwned.com, over 12 billion credentials were compromised online as of March 6, 2024. This staggering figure underscores the vulnerability of password-based authentication systems. Most (if not all) of these involve compromised passwords, and often expose not only a compromise to the originally affected domain or web application, but also multiple accounts utilizing the same email address and password.
Dynatrace Perform 2024: Making Waves While Navigating the Future of Cloud Innovation
By Ken Buckler on Mar 15, 2024 3:19:56 PM
The Dynatrace Perform 2024 conference delivered a plethora of insights and forward-looking perspectives this month. Throughout the conference, the event encompassed keynotes, breakout sessions, customer panels, and hands-on training, offering a holistic view of the latest trends and innovations in the tech industry. The overarching theme, "Make Waves," encapsulates the imperative for transformation and disruption in the tech industry. It underscores the need to drive substantial change and progress amidst evolving trends.
How DDI Engineers Earn a Seat at the Cloud Strategy Table
By Shamus McGillicuddy on Feb 20, 2024 11:53:05 AM
More than 41% of DDI (DNS, DHCP and IP address management) teams lack sufficient influence over their companies’ cloud strategies, according to my research. This stat was published in my market research report, “DDI Directions: DNS, DHCP, and IP Address Management Strategies for the Multi-Cloud Era.” The report was based on a survey of 333 DDI-focused IT professionals.
EMA Asked Network Pros: What Do Network Automation Vendors Need to Know About Your Challenges?
By Shamus McGillicuddy on Feb 15, 2024 9:34:49 AM
I will soon publish new market research about enterprise network automation strategies. The report is based on a survey of 350+ IT professionals and one-on-one phone interviews with a dozen experts from a variety of well-known enterprises, universities, and government entities.
HPE to Acquire Juniper Networks
By Shamus McGillicuddy on Jan 11, 2024 10:27:44 AM
HPE announced this week its intent to acquire Juniper Networks for $14 billion. When this deal closes, Juniper will combine with HPE's Aruba Networks division, which is itself a product of multiple acquisitions by HPE, including Aruba Networks (Wi-Fi and switching) and Silver Peak (SD-WAN and WAN optimization).
From AI to Zero Trust: Decoding Cybersecurity Trends for 2024
By Chris Steffen on Dec 22, 2023 4:09:04 PM
In 2024, we will continue to see globally significant advancements in information security and regulatory compliance spending for organizations of all sizes. From zero trust architecture to the integration of AI-driven solutions and the growing emphasis on regulatory alignment, 2024 will redefine how organizations safeguard sensitive information, navigate compliance complexities, and fortify their API ecosystems. Understanding and adapting to these transformative trends will be pivotal for businesses aiming to stay resilient, secure, and compliant in a time noted for rapid technological advancements and stringent regulatory landscapes. Here are our predictions for information security in 2024.
Black Hat Europe 2023: Navigating the Evolving Landscape of Cybersecurity
By Ken Buckler on Dec 22, 2023 3:47:45 PM
The Black Hat Europe 2023 conference, a gathering of cybersecurity professionals and experts, delved into the intricate world of cybersecurity, exploring emerging threats, innovative defense strategies, and the pressing need for collaboration between the private sector and government entities. Here's a breakdown of the key takeaways and highlights from a few of the conference sessions.
Tech at the Gap Decoded: A Look at Maryland’s “Best-Kept Secret” Technology Conference
By Ken Buckler on Oct 23, 2023 1:38:19 PM
Every year, technology enthusiasts and industry leaders gather at the serene Rocky Gap in Western Maryland for Tech at the Gap, an event that has earned the reputation of being one of the hidden gems of Maryland's tech conference scene. This year, the conference's theme, "Decoding Intelligence," promised to unveil the mysteries behind artificial intelligence and its transformative potential. With an impressive lineup of keynote speakers and breakout presenters, the event did not disappoint.
CMDB is alive and on the rise; cloud found innocent of its demise
By Valerie O'Connell on Aug 21, 2023 2:39:42 PM
Articles proclaiming the death of CMDB started appearing with regularity as early as 2010. Cloud was named as the likely killer. The problem with this bit of folk wisdom is that it isn’t true.
EMA experience and field research consistently find that CMDB use not only continues but is on the rise. In a 2022 EMA initiative on the rise of ServiceOps, 400 global IT leaders stated that CMDB use was central to major functions. For many of those respondents, CMDB use was viewed as increasing in importance for automation of complex processes.
Where is the disconnect?
Playing to Win: Generative AI, Cloud Security, and More at Black Hat 2023
By Ken Buckler on Aug 18, 2023 11:48:34 AM
The stage was set, the players were ready, and Black Hat USA 2023 delivered a cybersecurity spectacle that left no doubt—this was a game-changing event. As we unpack the highlights, one overarching theme emerges: a united front against ever-evolving threats. From generative AI to cloud security and a glimpse into the future of defense, this year's conference illuminated the power of collaboration and innovation. Amidst these pivotal discussions, one revelation—the TETRA:BURST vulnerabilities—took center stage, leaving an indelible mark on the field.
IT Nation Secure Conference Highlights Solutions to the People Problem in Cybersecurity
By Ken Buckler on Jun 13, 2023 6:39:53 AM
Last week, I had the privilege of attending ConnectWise’s IT Nation Secure conference. The three-day conference focused on managed service providers (MSPs) – specifically, how those MSPs can better secure and protect small businesses and midmarket companies. If you haven’t attended this conference in the past but have attended others, I highly recommend attending the ConnectWise IT Nation Secure conference due to the unique perspective they provide for the cybersecurity industry.
RSA Conference 2023: A “Stronger Together” Moment for Cybersecurity
By Ken Buckler on May 8, 2023 1:15:00 AM
The 2023 RSA Conference was one of the largest and most impactful cybersecurity events of the year. The conference brought together a large number of exhibitors, training sessions, and sponsor briefings and generated a lot of buzz on social media platforms, such as Twitter and LinkedIn. We took some time to analyze the data from social media and the conference and found some interesting trends.
Star Wars Day – How Security Failures Led to the Empire’s Downfall
By Chris Steffen on May 4, 2023 9:58:11 AM
To celebrate Star Wars Day, I thought I would share a few ways in which the Empire did not adhere to information security best practices, and that enabled the Rebels to win.
To be clear: I do not support the Empire, the Sith Lords, or any other types of scum and villainy. Nor am I trying to portray the Rebel Alliance as a weird, Force-wielding, Galactic hacker consortium or something. But had the Empire not been so lax in their security controls, Emperor Palpatine and his buddies might have been able to bring their “order and peace” to the galaxy.
What is ServiceOps? A research-based look at why it’s on the rise
By Valerie O'Connell on Mar 20, 2023 3:23:32 PM
A working definition: ServiceOps is a technology-enabled approach to unifying IT service and IT operations management for excellence in delivery of digital business services.
Although the two teams have different charters and skillsets, IT service and IT operations are inextricable. There is no service without effective IT operations.
How to Mitigate Multi-Cloud Networking Complexity
By Shamus McGillicuddy on Feb 22, 2023 1:08:03 PM
This is a sponsored blog post.
With most companies now operating in multiple cloud providers, network and security complexity are increasing. For instance, 96% of multi-cloud enterprises are using more than one networking vendor across their cloud estates, according to new research from Enterprise Management Associates (EMA).
The Harsh Truth About Layoffs in the Tech Industry
By Chris Steffen on Feb 14, 2023 10:48:37 AM
Seemingly every day, we hear about the next batch of layoffs from the household-name tech companies: 10,000 here, 1,700 there. As we continue into earning seasons for these publicly traded (and some not publicly traded) companies, we will likely hear more. The substory is that unemployment is at an all-time low, with the job market adding over 500,000 jobs in January.
A Valentine's Day Wakeup Call: The Heartbleed Vulnerability and the Urgent Need for Improved Cybersecurity
By Ken Buckler on Feb 14, 2023 6:05:20 AM
As of January 2023, Over 194,000 Systems on Internet Still Vulnerable to Heartbleed
The Bleeding Heart of the Internet
In April 2014, the Heartbleed vulnerability was publicly disclosed, sending the information technology world into a panic and rushing to patch this critical vulnerability in OpenSSL, which was allowing the theft of information directly from the memory of vulnerable systems, including private keys and other secrets. This vulnerability featured extremely easy exploitation by attackers, leaving no trace of attacks. Heartbleed ultimately resulted in many late nights for most of the information technology industry, who worked to implement and validate patches for open and closed source products that have integrated the OpenSSL libraries – which accounts for an extremely large percentage of technologies connected to the internet.
Graphiant: A Vendor to Watch
By Shamus McGillicuddy on Sep 8, 2022 12:16:28 PM
The WAN edge is becoming more distributed and dynamic, which is overburdening IT organizations that are already at a breaking point. Software-defined WAN technology has solved some of the issue, but they haven’t gone far enough. The cloud, the Internet of Things (IoT), and the work-from-home (WFH) revolution demand something more.
RSAC 2022 Closing Thoughts - Return of Cybersecurity Conferences to the Wild, Wild West Coast
By Ken Buckler on Jun 16, 2022 9:43:34 AM
It’s time to circle the wagons and defend the data and users
As the world reopens, the conference booths light with excitement and empty expo halls are once again filled with hustle and bustle. I thought it important to take a moment and look at what changed in the past two years and where the security industry has room for improvement. This was the first in-person RSA Conference, and likely the first major security conference at all for that matter, with large in-person attendance after the peak of the COVID-19 pandemic. While the conference looks very similar to conferences before the pandemic, the cybersecurity industry landscape has drastically changed.
Reflection on Informatica World 2022
By Will Schoeppner on Jun 9, 2022 3:45:15 PM
Recently, I had the opportunity to attend Informatica World 2022 (IW22) in Las Vegas. Returning to the in-person conference scene caused some apprehension; however, reflecting on takeaways and engaging in discussions around data integration made this trip a worthwhile experience. I want to thank IW22 for a thought-provoking week of discussions centered on data management, data integration, interoperability, artificial intelligence, and navigating a complex, hybrid, multi-cloud digital environment with Informatica experts, sponsors, and customers.
Intelligent Mice, Intelligent Mouse Traps – The Future of Cybersecurity and AI
By Ken Buckler on May 31, 2022 6:27:37 AM
Long gone are the days of simple, signature-based defenses against cyber-threats.
Cyber-threats are growing at an exponential rate in the perpetual cat-and-mouse game of cybersecurity, and traditional approaches to cybersecurity are struggling to keep pace. In 2021, anti-malware vendors estimated that they detected between 300,000 and 500,000 new pieces of malware every day. That means than in 2021 alone, over 100 million new pieces of malware were created. Even if cybersecurity vendors can keep up with the sheer volume of new pieces of malware, traditional signature-based and even heuristic-based detection algorithms will struggle to keep up – and that’s only for known malware.
How to Identify the Ideal Network Automation Solution
By Shamus McGillicuddy on Apr 27, 2022 9:00:18 AM
Data center network automation delivers four primary benefits to a business, according to Enterprise Management Associates research: operational efficiency, reduced security risk, improved compliance, and network agility.
Not so Quiet on the Cyber Front: Why Your Organization is Still a Target
By Ken Buckler on Mar 4, 2022 2:27:34 PM
It's been quite an interesting couple of weeks. What started off with rising tensions as Russia amassed troops at the Ukraine border evolved into a full invasion of the country. Our newsfeeds are filled with stories and images of ace fighter pilots, brave soldiers making their final stands, and farmers stealing Russian tanks by hooking them up to farm equipment – but another battle has been taking place behind the scenes for many years.
Cybersecurity Asset Management for Vulnerability Management: Key Capabilities, Benefits
By Chris Steffen on Feb 28, 2022 8:46:39 AM
This is the last in a three-part blog series by Enterprise Management Associates for Axonius discussing how vulnerability management can be expanded and simplified by using a cybersecurity asset management solution. In Part 1, we looked at how cybersecurity asset management can simplify vulnerability management and Part 2 focused on how a cybersecurity asset management solution improves an organization’s vulnerability management program. Part 3 of the series provides a brief summary and some perspectives on the benefits of a cybersecurity asset management solution as it relates to vulnerability management.
Accelerate Network Automation by Pivoting From Homegrown to Commercial Software
By Shamus McGillicuddy on Feb 24, 2022 8:11:24 AM
Sponsored post for Gluware
Improving Vulnerability Management With Cybersecurity Asset Management
By Chris Steffen on Feb 17, 2022 10:08:25 AM
This is the second in a three-part blog series by Enterprise Management Associates for Axonius discussing how vulnerability management can be expanded and simplified by using a cybersecurity asset management solution. In Part 1, we looked at how cybersecurity asset management can simplify vulnerability management. Part 2 of the series focuses on how a cybersecurity asset management solution improves an organization’s vulnerability management program.
Simplify Vulnerability Management With Cybersecurity Asset Management
By Chris Steffen on Feb 10, 2022 9:41:39 AM
This is the first in a three-part blog series by Enterprise Management Associates (EMA) for Axonius discussing how vulnerability management can be expanded and simplified by using a cybersecurity asset management solution. Part one of the series focuses on defining the cybersecurity asset management solutions category and includes a summary definition of vulnerability management.
NetOps and SecOps Partnerships Flourish With Modern DDI Technology
By Shamus McGillicuddy on Nov 17, 2021 8:50:01 AM
More than 75% of enterprises are reporting increased collaboration between their NetOps teams and SecOps teams , according to EMA's new research on NetSecOps partnerships. Digital transformation is a significant driver of this collaboration. About four out of five enterprises reported that NetSecOps collaboration is in response to public cloud adoption, work-from-anywhere initiatives, data center modernization, the internet of things, and edge computing.
Data Security in a Multi-Cloud World...
By Chris Steffen on Jul 22, 2021 8:24:36 AM
Five Key Identity Governance Features That Your Identity and Access Management Solution Does NOT Support
By Steve Brasen on Mar 18, 2021 9:23:32 AM
Since the start of the COVID-19 pandemic, identity management has taken center stage as the key enterprise security practice for enabling remote workforces while protecting company data and IT services. Though much of the media hype has focused on evolving technologies in enterprise identity and access management (IAM)—such as enabling passwordless and multifactor authentication—it is often overlooked that identity governance and administration (IGA) is experiencing its own renaissance not only due to pandemic-related access requirements, but also in support of recently-enacted compliance regulations, such as the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
F5 / AWS Integration Podcast...
By Chris Steffen on Oct 20, 2020 9:35:31 AM
I had the opportunity to participate in a podcast with the team at F5. Christine Puccio – VP of Global Cloud Alliances and Heath Parrott – Senior Global Solutions Architect for Cloud discussed their latest announcement: the integration between F5 Essential App Protect, a web application firewall (WAF) SaaS solution and Amazon CloudFront, a content delivery network (CDN) solution from Amazon Web Services (AWS).
F5 WAF / AWS CloudFront Integration...
By Chris Steffen on Oct 20, 2020 8:00:00 AM
Recently, I had the opportunity to participate in a podcast with the team at F5. Christine Puccio – VP of Global Cloud Alliances and Heath Parrott – Senior Global Solutions Architect for Cloud discussed their latest announcement: the integration between F5 Essential App Protect, a web application firewall (WAF) SaaS solution and Amazon CloudFront, a content delivery network (CDN) solution from Amazon Web Services (AWS). Before discussing the announcement specifically, I thought it would be best to provide a bit of insight into these complementary technologies.
Why Consumer IAM is Fundamentally Different From Traditional IAM
By Steve Brasen on Oct 6, 2020 9:34:58 AM
Identity and access management (IAM) has been an integral part of IT since the early days of computing. Foundational to the security of IT resources is the need to identify who may access them, and placing limits on what they can do with them. Since these requirements were principally established to support internal business processes, IAM practices and technologies evolved to specifically support business employees. Following the introduction of the internet, however, new security challenges evolved in support of ecommerce. Rather than having to support a limited number of employees, businesses now must ensure the secure delivery of digital engagements with an expansive range of customers and marketing prospects. These challenges greatly accelerated over the last two decades due to the rise in popularity of consumer-focused cloud services and increasing user mobility.
Three Opportunities to Create Positive Experiences with Consumer IAM
By Steve Brasen on Sep 10, 2020 2:53:42 PM
One-half of one second—that is how brief of a time-span it seemingly can take for a business to lose a customer. Gaining and retaining consumer attention is something of a nuanced art form and science that can be completely undone by an easily misplaced word or a cumbersome process. Businesses frequently lose customers not because they have an inferior product or service but simply because, for some reason, the customers had a brief negative experience. While it is impossible to control what customers are thinking and feeling at any given time, it is clear that many of these negative impressions are self-inflicted by businesses that fail to create welcoming environments. Unfortunately, many organizations find it difficult to adopt CIAM approaches that enable favorable consumer experiences without violating security requirements. After all, the primary purpose of CIAM is to protect a business’s intellectual property, secure private customer information, and prevent account misuse or fraud.
Entrants in the Unified Analytics Warehouse Race
By John Santaferraro on Aug 26, 2020 2:59:08 PM
As the race to deliver the UAW heats up, EMA sees the following vendors working toward a convergence of the data warehouse and data lake: Ahana, Amazon, Cloudera, Databricks, Dremio, Google, HPE Ezmeral, Incorta, isima.io, Oracle, SAP, Starburst, Teradata, and Vertica. EMA also anticipates that vendors that successfully deliver a unified analytics warehouse will quickly eclipse data warehouse and data lake vendors, making them obsolete, except for targeted use cases and analytical projects.
The Requirements for a Unified Analytics Warehouse
By John Santaferraro on Aug 21, 2020 12:38:29 PM
To assess the likely winners in the race for the unified analytics warehouse, it is important to understand the various requirements of modern analytics programs and the unified analytics warehouse.
The Emergence of the Unified Analytics Warehouse
By John Santaferraro on Aug 21, 2020 12:37:39 PM
The race for a unified analytics warehouse is on. The data warehouse has been around for almost three decades. Shortly after big data platforms were introduced in the late 2000s, there was talk that the data warehouse was dead—but it never went away. When big data platform vendors realized that the data warehouse was here to stay, they started building databases on top of their file system and conceptualizing a data lake that would replace the data warehouse. It never did.
Five Reasons Consumer IAM is Indispensable in the New Normal
By Steve Brasen on Aug 19, 2020 11:33:19 AM
When regional stay-at-home orders in response to the COVID-19 pandemic were first issued in early 2020, the general expectation was that societal changes would only be temporary. As people hunkered down in homes around the world, they expressed a collective confidence that life would eventually (perhaps after only a few weeks) return to normal. Over time, the realization that the pandemic has, in many ways, changed the world forever has slowly been gaining acceptance. Of course, it seems likely that at some point medical science will discover the means to control and perhaps even eradicate the illness, and eventually people will feel free to emerge from their homes. However, many of the fundamental changes to day-to-day activities and lifestyles that have been adopted are likely to persist well into the future.
Digital Marketing - Find the Right Media to Create a Dialogue
By John Santaferraro on Apr 22, 2020 2:21:33 PM
Syndicate, Syndicate, Syndicate
We are a multi-media generation that offers unlimited media choices to information consumers. Buyers can choose from mobile apps, videos, websites, podcasts, or printed media. They consume infographics, eBooks, whitepapers, slide shares, webinars, interactive sites, and e-learning systems. They can find their media via search, social streams, mashups, or journalistic consolidation sites.
Digital Marketing - Understand How People Buy
By John Santaferraro on Apr 22, 2020 2:12:48 PM
The Magic of the Buying Cycle
Increasing sales and revenue with digital marketing involves far more than generating leads. Too many marketers have focused their efforts almost entirely on demand generation at the expense of proactively moving leads through the funnel and closing more deals. EMA supports a balanced digital marketing approach that focuses on moving buyers forward at all points in their buying journey.
Digital Marketing - Know the Person You Want to Target
By John Santaferraro on Apr 22, 2020 1:42:22 PM
The Search for the Right Persona
Savvy marketers want to better understand buyer personas relevant to the products and solutions in their portfolio. However, not every marketer understands the importance of prioritizing the search for the right persona. Persona creation can be laborious and getting agreement on personas can be even more challenging, but it is worth the effort. Once you create a persona, it becomes the guide for every person in your organization entering a dialogue with a customer or potential buyer.
How Knoa’s User Experience Management can Optimize RPA for Value
By Dennis Drogseth on Apr 16, 2020 11:21:20 AM
UEM for user experience management and RPA for robotic process automation are two IT acronyms that continue to elude well-understood definitions, albeit for somewhat opposite reasons. UEM goes back decades, first emerging out of primarily network-centric management, becoming a cornerstone of business service management, and later being consumed by application performance management (APM) much to its own detriment. RPA is comparatively recent, evolving out of screen scraping into far richer technical options that are diverse in nature, with many RPA vendors contending with and replacing the more consultancy-driven platforms for business process management (BPM).
Prioritizing Security When Selecting A Video Conferencing Solution...
By Chris Steffen on Apr 10, 2020 9:08:08 AM
Before the recent COVID -19 pandemic, most companies looked at unified communications and collaborations (UC&C) solutions as important technology often used by sales and marketing teams as part of their process, but not necessarily a critical part of the business infrastructure. With work from home (WFH) becoming the mandated norm, businesses have come to look at UC&C solutions as mission-critical tools, allowing managers and leaders to communicate with their employees and employees to conduct some semblance of normal business.
FBI Warns of Coronavirus Scams
By Chris Steffen on Mar 23, 2020 11:08:03 AM
On Friday, the FBI released an alert warning of increased scams related to the Coronavirus outbreak. From the FBI announcement:
Righting a Wrong: IBM is a Leader in the Cloud...
By Chris Steffen on Mar 13, 2020 11:38:19 AM
A article was recently released by Bloomberg news discussing the market share of various cloud providers, and their methods and rankings need to be re-examined.
Creating Personalized, Targeted Webinars
By John Santaferraro on Mar 10, 2020 6:55:41 PM
The best webinars are personalized and targeted. They are personalized by carefully considering and engaging those who will be attending the webinar. They are targeted by understanding the buying phase and persona of the audience. In other words, a webinar created with the audience in mind maps perfectly into digital marketing strategies created and carefully considers the different stages of the buying cycle. This is the way we do webinars here at EMA.
10 Creative Options for Your 2020 Webinars
By John Santaferraro on Mar 10, 2020 6:44:31 PM
Webinars are boring…until you think outside the box and utilize creative ideas to wake up the minds of your attendees. Pick one of these ten creative options to revitalize your webinars in 2020.
Engaging, Inspirational Webinars Drive the Most Leads
By John Santaferraro on Mar 10, 2020 6:34:01 PM
“Webinars are boring!” I’ve heard those exact words from both marketing leaders and webinar attendees. And for the most part it’s true. If you are still doing webinars in which the third-party pundit speaks first, then your company spokesperson gives a product pitch, your audience is probably mumbling those same words.
Security Awareness - Tax Scams 2020
By Chris Steffen on Mar 10, 2020 3:00:02 PM
Few people like the process of completing their taxes every year. But no one wants to be scammed out of the monies owed to them by the government. Be especially careful about those that contact you regarding your taxes, and confirm the sources of those emails and calls whenever possible.
Cisco becomes a Merchant Silicon Vendor, Launches a Disaggregated Super-Router
By Shamus McGillicuddy on Dec 12, 2019 10:44:41 AM
Five years and $1 billion in R&D investment has led to this. Cisco has positioned itself to be a jack-of-all trades routing supplier to network service providers and web-scale data center operators.
Top 5 Reasons You’re Spending Way Too Much Time, Energy, and Money on Modern Endpoint Management
By Steve Brasen on Nov 26, 2019 9:47:50 AM
The Transformational Promise of Per-Application ADCs
By Shamus McGillicuddy on May 23, 2019 11:09:45 AM
Today’s cloud-centric enterprises require agile infrastructure that can scale up and down as capacity requirements evolve. Nowhere is this shift in infrastructure requirements more apparent than in the world of application delivery controllers (ADCs) and load balancers. Today’s enterprises are shifting away from monolithic ADC appliances in favor of lightweight, per-application software ADCs and load balancers.
SAP Set to Revolutionize Cloud Intelligence for Business Professionals
By John Santaferraro on May 23, 2019 9:27:33 AM
At SAPPHIRE Now 2019, SAP introduced new cloud services that reach far beyond their installed base and make them a solid option for anyone looking for application or analytics solutions in the cloud. The new data and analytics offerings are not a departure from their commitment to current customers; they extend increased business value for all medium and enterprise companies looking for rapid return on their cloud investments.
Datastax Ready for Next-Generation Cloud and Mobile Application Delivery
By John Santaferraro on Jan 28, 2019 1:53:12 PM
Two primary streaks of innovation drive the need for more flexible, scalable technology at the start of the 2020s. First, digital and mobile business models continue to push organizations to expand their use of data far beyond traditional, structured, and centralized data management. The promise of big data platforms to easily allow for global data collection and analysis has never been realized. Second, modernization and innovation cycles that used to recur every five to seven years have been condensed. Most organizations trying to stay ahead of digital transformation are not ready for the speed and agility necessary to maintain a competitive advantage in a digital world.
In summarizing the teachings of Charles Darwin, Louisiana State University business professor Leon C. Megginson said the following at a convention of the Southwestern Social Science Association:
“It is not the strongest of the species that survives, nor the most intelligent that survives. It is the one that is the most adaptable to change.”
Celonis Process Mining: A Modern Value Creation Engine for the Digital World
By John Santaferraro on Dec 12, 2018 8:18:10 PM
Process mining technology extracts business application data, tags it based on time and location within a business process, visualizes the business processes, logs variations, and makes recommendations for process improvement based on built-in advanced analytics. RPA technology identifies repetitive business processes with potential for automation and codifies the logic necessary to take intelligent action without human intervention. In some more critical areas, the RPA engine makes recommendations for validation by human decision-making.
Tableau Sets the Tone for Business Intelligence 2019
By John Santaferraro on Nov 7, 2018 11:57:56 AM
From community to consumers of data, Tableau Conference 2018 (TC18) set the tone for the business intelligence market in 2019.
Salesforce Honors Customers, Boosts Sales Productivity: Gleanings from an Industry Analyst Observer
By John Santaferraro on Oct 9, 2018 12:44:15 PM
I could spend pages and days talking all about the new technology that was released at Dreamforce 2018, but I am going to take the higher road and discuss what Dreamforce 2018 means to customer organizations. Salesforce demonstrated that it cares about its customers and is committed to increasing the productivity of customer-facing teams around the world. Of course, if customer-facing teams are more productive, that will mean increased revenue, higher customer satisfaction, and a palpable competitive advantage.
The C-Suite Should see Gains in Productivity and Profitability
Many sales leaders complain about the challenge of getting sales representatives to enter information into their sales automation systems. The results are incomplete information and the inability to properly forecast and manage sales teams for success. The introduction of Einstein Voice allows sales teams to interact with Salesforce products over their morning coffee or handsfree on their drive home, freeing them to do more of what they are paid to do: sell.
Cyber Attackers Turn Their Sight to ERP Applications
By Paula Musich on Sep 26, 2018 7:58:29 AM
In late July, the Department of Homeland Security issued a warning about a growing number of malicious cyberattacks aimed at ERP systems based on a research project conducted by Digital Shadows and Onapsis. This warning comes at the heels of the first-ever DHS CERT Alert focused on SAP Business Applications released in May of 2016. According to the report, hackers exploited old, unpatched vulnerabilities to successfully hack multiple organizations, including government agencies, energy businesses, and financial services companies. Onapsis and Digital Shadows found significant evidence of increased interest on ERP applications, including bad actors in criminal forums on the dark web asking for exploits specifically targeting ERP technology vulnerabilities. The study, “ERP Applications Under Fire: How Cyberattackers Target the Crown Jewels,” found that the attackers do not need to use advanced techniques to breach their targets because the current state of ERP application security across organizations is such that old vulnerabilities still affect these systems. This means that attackers don’t need to develop new zero-days or advanced exploitation techniques.
EMA Perspectives – Informatica Makes Sparks Fly in the Cloud
By John Santaferraro on Sep 18, 2018 11:54:08 AM
On September 12, 2018, at Strata NYC, Informatica announced a data management solution for Apache Spark-based cloud environments, including Google Cloud Dataproc, Qubole, and Azure Databricks. Touting new advancements in CLAIRE™, a metadata intelligence technology powered by artificial intelligence (AI) and machine learning, this new release is targeted at increasing the efficiency and reach of data management organizations. To expand efficiency, Informatica is releasing more than 50 new algorithms and functions for automated data discovery and preparation, as well as machine learning focused on industrializing data operations.
Public Clouds Are Disrupting Enterprise Network Management
By Shamus McGillicuddy on Sep 14, 2018 3:31:41 PM
Network managers who are supporting the migration of critical applications to the public cloud will need a new set of tools for engineering and operations.
3 Key Lessons from DockerCon 2018: Strategic Analysis of the Container Market Place
By Torsten Volk on Jun 26, 2018 5:21:30 AM
Today, where there are almost as many approaches to digital transformation as there are enterprise software vendors, Docker refocuses its strategy on providing the best unified container management platform for DevOps. Docker’s key value proposition is to enable developers to build an application once and then deploy it to any Kubernetes-driven private or public cloud, where DevOps teams and IT operations can manage it throughout its lifecycle and move it to another location at any point in time. However, Docker also aims to absorb traditional enterprise applications, edge and IoT workloads, big data apps, blockchain, and serverless functions, both on Windows and on Linux.
Future-Proofing Your EDR Solution
By Steve Brasen on Jun 19, 2018 5:16:04 PM
EMA recently published primary research on the topic of “Adopting Effective Solutions in Endpoint Detection and Response,” which included a detailed comparison of two of the most popular platforms on the market today: Tanium and 1E Tachyon. Put simply, Endpoint Detection and Response (EDR) solutions represent a classification of management tools designed to proactively provide the holistic visibility and rapid automation necessary to respond to endpoint security threats and administration requirements in real-time. The purpose of the evaluation was to provide an example of how to conduct a side-by-side comparison of EDR solutions in order to determine the optimal platform for meeting current endpoint management requirements.
Cisco Live 2018: Forget Hardware, Cisco Is All About Software
By Shamus McGillicuddy on Jun 14, 2018 4:17:51 PM
For years network engineers have built lucrative careers upon their wizardly knowledge of things like network protocols, hardware specifications, and the Cisco command line interface (CLI). These skills are still essential to network engineering, but they are emblematic of a highly manual, box-by-box era of network engineering and operations. Today’s enterprises need agile, programmatic networks that leverage software, automation, and more
Putting the User into “User Experience Management”
By Dennis Drogseth on May 31, 2018 8:05:11 AM
In the course of researching, documenting and advising on user experience management needs and directions for more than a decade, I’ve found myself waging a quiet (and sometimes not so quiet) war with several industry assumptions. Chief among these is the notion that user experience management (UEM) is purely a subset of application performance management (APM). This APM-centricity misses some of UEM’s most critical value points, and in a basic sense fails to recognize what UEM is truly about.
Thoughts and Lessons Learned From an Analyst and CISO Conference
By David Monahan on May 15, 2018 8:52:00 AM
The week of April 30, 2018, I spent a few days in the great city of London at “The IT security Analyst and CISO Forum,” a small, invitation-only event hosted by Eskenzi PR and Marketing. It was my first year at the event, so I wasn’t sure what to expect. After I arrived, it was obvious the Eskenzi PR team had this event down. It was well orchestrated and executed, and the entire team was very professional.
Understanding Network-as-a-Service from Alcatel-Lucent Enterprise
By Shamus McGillicuddy on Mar 19, 2018 10:44:00 AM
Editor’s note: This blog post was sponsored by Alcatel-Lucent Enterprise, but the sentiments are entirely my own.
What is Advanced Network Analytics? Cutting Through the Hype
By Shamus McGillicuddy on Feb 19, 2018 10:26:00 AM
Everyone wants to talk about how analytics is the future of network engineering and operations. The phrase “network analytics” is used by vendors of various stripes to imply that a particular technology is smarter and better than the average solution.
Solve the Cloud Networking Conundrum With SD-WAN
By Shamus McGillicuddy on Jan 9, 2018 2:41:04 PM
Enterprise networking professionals have a cloud problem, even if they don’t know it. Software-defined WAN (SD-WAN) solutions can help them solve this problem.
CA Technologies Pushes for Diversity in Tech Industry
By Shamus McGillicuddy on Nov 16, 2017 2:41:03 PM
Despite what you hear from trolls, bigots, and misogynists, diversity in the technology industry is a good thing. But the philosophy of diversity needs more champions. Tech companies and IT organizations need to expand their workforce beyond the herds of white men that have dominated the industry for decades.
SDN and the Data Center of the Future
By Shamus McGillicuddy on Oct 16, 2017 12:42:17 PM
Despite some recent obituaries published by my peers, software-defined networking is not dead. But perhaps certain aspects of it are dead or dying. If that’s the case, I say: “SDN is dead. Long live SDN.”
Transforming End-User Support – What Does It Mean and What Is It Really About?
By Dennis Drogseth on Sep 26, 2017 3:03:33 PM
I admit, “end-user support” sounds kind of old-fashioned. But in many respects just the opposite is true. In the digital age the need for easy access to new services is on the rise, and even with a much ‘hipper’ (and increasingly impatient) end-user population, the need for support and guidance remains. It is just taking different forms than in the past.
Machine Learning and Artificial Intelligence: The Promised Land for Lowering IT OPEX, Decreasing Operational Risk and Optimally Supporting Business Goals
By Torsten Volk on Sep 26, 2017 10:44:15 AM
What should machine and artificial intelligence (ML/AI) do for IT operations, DevOps and container management? The following table represents my quick outline of the key challenges and specific problem ML/AI needs to address. The table is based on the believe that ML/AI needs to look over the shoulder of IT ops, DevOps, and business management teams to learn from their decision making. In other words, every virtualization administrator fulfills infrastructure provisioning or upgrade requests a little bit differently. Please regard the below table as a preliminary outline and basis for discussion. At this point, and probably at no future point either, I won't claim to know the 'ultimate truth.'
Network Operations and Analytics from CA Technologies has Won the EMA Innovator Award
By Shamus McGillicuddy on Sep 5, 2017 12:42:17 PM
Network Operations and Analytics from CA Technologies has been named a winner of Enterprise Management Associates’ Innovator Award, which recognizes products and services that demonstrate true innovation in the IT industry and address the most critical challenges IT organizations face today.
The Internet of Things will Drive Network Management Evolution
By Shamus McGillicuddy on Jul 26, 2017 3:34:24 PM
EMA research has determined that network managers will need to upgrade, expand, and adapt their network monitoring and management tools and practices if they are going to support the Internet of Things (IoT).
Optimizing the Business With Network Analytics
By Shamus McGillicuddy on Jun 7, 2017 3:36:32 PM
Some network operations teams are discovering that they possess a critical asset that can transform enterprises: network data.
Q&A From How Digital Business is Shaping the Next Wave of Automation Webinar
By Dan Twing on Jun 5, 2017 8:14:06 AM
I recently presented findings from my Workload Automation (WLA) research and other EMA research on a webinar with Tim Eusterman, Sr. Director Solutions Marketing at BMC in a webinar titled “How Digital Business is Shaping the Next Wave of Automation”. The recording of the webinar is now live here, and the slides are available here.
ExtraHop Addy applies cloud-based machine learning to network data
By Shamus McGillicuddy on May 7, 2017 3:36:29 PM
IT analytics vendor ExtraHop unveiled a cloud-based service that applies machine learning heuristics to the metadata that its appliances generate from packet stream analysis. The service should give users better visibility into IT service problems and security threats.
The Open Networking Foundation’s New Direction: We Live in a Post-OpenFlow World
By Shamus McGillicuddy on May 6, 2017 3:36:32 PM
The Open Networking Foundation (ONF) recently unveiled plans to redefine itself for the post-hype phase of software-defined networking (SDN). I welcome the ONF’s reset and believe it bodes well for the industry’s future.
Redefining the Branch Office With SD-WAN
By Shamus McGillicuddy on May 5, 2017 3:36:32 PM
Editor’s Note: This blog post is sponsored by Citrix. The ideas and analysis are entirely the authors own.
Advanced IT Analytics: Making it Simpler to Optimize What’s More Complex
By Dennis Drogseth on Apr 13, 2017 3:03:33 PM
The growing market for analytics in IT is one of the more exciting areas to watch in the technology industry. Exciting because of the variety and types of vendor innovation in this area. And exciting as well because our research indicates the adoption of advanced IT analytics supports data sharing and joint decision making in a way that’s catalytic for both IT and digital transformation.
InterConnect 2017 – Showing off a whole New IBM
By Torsten Volk on Apr 10, 2017 1:19:45 PM
“Today, a dev team leveraging Kubernetes containers can get a cloud app up in minutes.” This statement by Arvind Krishna, IBM’s GM for Hybrid Cloud, at the beginning of his InterConnect 2017 keynote should have received a lot more recognition than it did. This one sentence shows the fundamental shift in IBM’s strategy, away from the old Tivoli-centric IT ops company and toward a modern DevOps-focused organization that is looking for differentiation up the stack. Today’s IBM encourages developers to deploy entire application environments without IT administrators even being aware.
Cisco introduces “Digital Building” Catalyst switches for IoT
By Shamus McGillicuddy on Feb 10, 2017 5:03:17 PM
Cisco recently announced a new series of Catalyst “Digital Building” switches. These Catalyst switches are designed for connecting and powering Internet of Things (IoT) devices and systems in smart buildings and other related environments. For example, one design innovation is the use of a separate power plate for Power over Ethernet (PoE), so even when an administrator reboots the device or updates its software, the switch will continue to deliver power to peripheral devices such as smart lighting and surveillance cameras.
Juniper founder steps away to run new startup Fungible: What is Fungible?
By Shamus McGillicuddy on Feb 10, 2017 10:45:30 AM
What is Fungible, Inc., the new startup created by Juniper Networks’ founder Pradeep Sindhu, working on?
Unified Endpoint Management: Bringing Multi-Device Support to the Next Generation of Business Professionals
By Steve Brasen on Jan 31, 2017 4:16:42 PM
It’s hard to believe there was actually a time before mobile devices. It wasn’t even all that long ago. In fact, this month Apple is celebrating the 10th anniversary of the iPhone. While the iPhone was not the first smartphone, its introduction is credited with kick-starting the mobile revolution and initiating the “consumerization of IT,” forever changing how technology is developed, marketed, and utilized in business environments. In trying to relate these historical milestones to Millennials, I find myself more and more sounding like a crotchety old man: “Back in my day, we only had PCs—and we were glad to have ‘em, too!” Today, three-quarters of all business workers regularly use mobile devices to perform job tasks, so my nostalgic recollections of PC-only business environments are increasingly falling on disinterested ears.
Dell EMC Opens Door to Bare-Metal Campus Switching
By Shamus McGillicuddy on Jan 26, 2017 2:02:37 PM
Back when Dell EMC was still just known as Dell, its networking business staked out a leadership position by becoming the first mainstream switch manufacturer to embrace bare-metal data center switching. Now it’s moving into the bare-metal campus switching market, too.
Avaya’s Chapter 11 bankruptcy filing points to a sale of its networking business
By Shamus McGillicuddy on Jan 26, 2017 2:02:37 PM
Avaya will restructure its debt under the protection of a Chapter 11 bankruptcy filing. The company aims to emerge from this action intact with minimal impact on customers. However, it is very possible that Avaya will sell its network infrastructure business.
The Software-Defined Future of the WAN
By Shamus McGillicuddy on Jan 26, 2017 2:02:36 PM
Software-defined networking (SDN) exploded onto the scene five years ago with a tremendous amount of hype, but the transition from hype to reality has been a little less explosive. Most enterprises are still in evaluation mode with SDN.
How Network Infrastructure Teams Support the Internet of Things
By Shamus McGillicuddy on Jan 26, 2017 2:02:36 PM
[Editors Note: This blog post is sponsored by Infosim®, but the ideas expressed here are entirely my own]
EdTech Networkers: Be Ready for Cloud, SDN, and IoT this Year
By Shamus McGillicuddy on Jan 26, 2017 2:02:35 PM
This sponsored blog post was originally published at at HelpSystems.com
Cisco DNA is Marchitecture, But Also a Shift Away From CLI
By Shamus McGillicuddy on Jan 26, 2017 2:02:35 PM
The industry has seen plenty of marchitectures from Cisco and its peers over the years. Its newest one, Digital Network Architecture (DNA), feels different, especially after I spent a week at Cisco Live 2016. DNA is different because underneath all the slideware and demos is an apparent commitment to changing the way enterprises do networking. In other words, Cisco wants network engineers to rely less on their skills with its command line interface (CLI).
Preparing Network Management for SDN and NFV
By Shamus McGillicuddy on Jan 26, 2017 2:02:34 PM
[Editor’s note: This blog is sponsored by Infosim®, but the content is entirely my own]
Network Managers Should be Monitoring Servers
By Shamus McGillicuddy on Jan 26, 2017 2:02:33 PM
Editor’s Note: This article was originally published by HelpSystems on February 2, 2016.
Early Adopters Define SDN
By Shamus McGillicuddy on Jan 26, 2017 2:02:33 PM
Greg Ferro recently blogged about how attempts to define software-defined networking (SDN) are a waste of time. He wrote:
The Benefits of Leveraging MSPs for Performance and Security Monitoring
By Shamus McGillicuddy on Jan 26, 2017 2:02:32 PM
[Author’s Note: This post is sponsored by Edgeworx. The content is entirely mine.]
The Truth Behind the Scope of the Endpoint Problem in the Enterprise
By David Monahan on Jan 12, 2017 6:41:06 PM
The Evolution of the “Endpoint”
Over the past few years, the perception of what an “endpoint” is, and therefore the definition, has changed. The original perception was a user workstation independent of operating system. With the expansion of functionality, data persistence, Internet connectivity, and ultimately the threats against them, that definition no longer applies. Laptops became included, then smartphones, servers, tablets, internal file shares, and dedicated or special function devices such as point of sale terminals and processors.
Analytical Resolutions for Technologists and Tech Teams in 2017
By John Myers on Jan 5, 2017 9:03:35 AM
Ahhh, the annual resolutions list! A time-honored tradition when we all look at the new year as an opportunity for a fresh start.
PODCAST: Discussing Big Data, Integration and Security
By John Myers on Jan 5, 2017 9:03:34 AM
Dos and Don’ts for the Data Scientist
By John Myers on Jan 5, 2017 9:03:34 AM
Review of Statistics Done Wrong by Alex Reinhart
Since the advent of the big data era, organizations have been crying out for data scientists. Initially it was finding the true data scientist. But as these resources were considered scarce, it was a search for people who could hand-code analytical models in a Hadoop environment. As statistical tools such as R, Alteryx, and RapidMiner augmented Hadoop environments, we started to include traditional tools such as SAS and SPSS. These data scientists, or data scientists in training, were asked to take large amounts of data and divine the nuggets that would create a “cross-sell/up-sell” recommendation engine that would launch the next Netflix or link two disparate data sets that explain how markets interact and find the next groundbreaking investment opportunity.
PODCAST: Cloud Data Warehousing
By John Myers on Jan 5, 2017 9:03:34 AM
Big Data and the Data-Driven Enterprise
By John Myers on Jan 5, 2017 9:03:34 AM
How the EMA HDE Information Management Layer Impacts the Growth of Analytical Platforms
By John Myers on Jan 5, 2017 9:03:32 AM
The ability to execute in a low latency time frame is a core component of the concept of next generation data management architectures such as the Enterprise Management Associates Hybrid Data Ecosystem (HDE). One of the key business drivers of the HDE is speed of response, which stems from an organization’s drive to execute faster than their competitors to create an advantage or to be on par with those competitors to simply “keep up with the Joneses.” You see this in workloads such as cross-sell/up-sell opportunities for revenue generation. You see this in opportunities to limit costs with asset logistics and labor scheduling optimization. You see this in opportunities to limit exposure to risk in fraud management and liquidity risk assessment.
A Tribute to IoT Device Security Researchers
By David Monahan on Jan 3, 2017 9:34:22 AM
This blog in the Internet of Things (IoT) series comes as a tribute to security researchers everywhere. The autumn’s largest security-focused show is the Black Hat Security conference. If you are not familiar with Black Hat, it is a tech conference that started in 1997 and covers numerous security topics in various presentations that are fairly to highly technical. As mentioned in the first blog in the series, IoT-like systems have been around a long time. However, researchers began paying more public attention to IoT around 2011. Visibility on the subject of the security, or lack thereof, of IoTincreased in 2011, when researcher Jay Radcliffe demonstrated that medical devices; in this case, his own automated insulin pump, could be hacked to deliver a lethal dose of insulin.1 Since that time, there were numerous other IoT hacks in various fields, including:
IoT Enterprise Risk Report
By David Monahan on Dec 21, 2016 2:47:12 PM
ForeScout recently released an IoT Enterprise Risk Report based on research from ethical hacker Samy Kamkar. Based on Kamkar’s findings, the report on IoT security issues could readily be renamed something like, “IoT: the bane of the enterprise environment,” or “IoT brings new meaning to the term ‘Enterprise Risk’.”
Acronym Acrobatics: Relating UEM to UEM
By Steve Brasen on Dec 6, 2016 11:14:30 AM
An unfortunate side effect of maintaining a vibrant technology subculture is an over-reliance on acronyms to describe basic concepts and solutions. For instance, to be ITIL compliant a CTO may need to invoke the ARP of a TCP or UDP IPv6 WAN to determine the DNS entry of an SMTP server for a POS system to prevent GIGO and ensure WYSIWYG. Now, if you understood that statement, you are certainly among the lucky few “in the know” and probably use these terms on a regular basis. However, if you are unfamiliar with or had to look up any of those terms, you likely recognize the core problem. While acronyms are intended to simplify complex technical conversations, they actually impede successful communication if any participants are unaware of their meaning. Sometimes acronyms are introduced to shorten long-winded technobabble; sometimes they are developed as marketing devices to create unique sounding products; and often they evolve simply because they make techno-elitists sound more knowledgeable.
How to Unleash the Full Value of Hybrid Cloud
By Torsten Volk on Nov 9, 2016 4:03:28 PM
In an ideal world, customers would be able to fully take advantage of the benefits of hybrid cloud by rationally matching infrastructure parameters -cost, performance, reliability, availability, security, regulatory compliance, scalability- with the requirements and dependencies of each application.
VMware and OpenStack: A Marriage Made in Heaven?
By Torsten Volk on Nov 9, 2016 4:00:28 PM
As we -Evan and I- were ranting last week about how OpenStack and VMware fit together (see #EMACloudRants), we were mainly focusing on the central conundrum that VMware faces within this context: “Should we support an open platform that could commoditize away a substantial part of our profitable infrastructure business or should we ignore the threat and do our own thing”
Software Defined Storage: The Vendor Landscape – Part 2 of 2
By Torsten Volk on Nov 9, 2016 4:00:27 PM
As promised in my previous post on “Software Defined Storage – Why Customers Should Care”, I want to follow-up with a brief overview of the competitive landscape.
EMA Cloud Rants – Pilot Episode
By Torsten Volk on Nov 9, 2016 4:00:27 PM
Evan Quinn and I have been collecting popular customer questions for a while and wanted to share our thoughts on these questions in the form of a new format: EMA CLOUD RANTS. Each week we will discuss one of the hot topics in enterprise IT to provide the viewer with rapid analyst insights, without any fluff. Here goes the first one:
The State of the Software Defined Data Center
By Torsten Volk on Nov 9, 2016 4:00:26 PM
Of course, I always encourage practitioners to carefully study the full EMA research report on the “Obstacles and Priorities on the Journey to the Software-Defined Data Center” or at least read the research study summary or at the very least join the EMA SDDC Research webinar on February 18, but I still want to briefly summarize the key findings here.
EMA Research: Enabling Enterprise IT Management to Optimally Support Big Data
By Torsten Volk on Nov 9, 2016 4:00:26 PM
What does Big Data mean to traditional enterprise IT? Organizations of any size and industry are becoming more and more aware of the incredible importance of capturing, managing and analyzing the data available to them. The more comprehensively companies are able to tap structured and unstructured data sources, the quicker they can refresh this data and the more successfully they make this body of data available to all business units, the better they can develop advantages in the market place. Today’s business units are demanding the rapid implementation of these big data use cases, as well as optimal resiliency, cost efficiency, security and performance.
Software Defined Storage: Why Customers Should Care – Part 1 of 2
By Torsten Volk on Nov 9, 2016 4:00:26 PM
Much marketing hype and heated discussions should be seen as excellent indicators for the fact that Software Defined Storage (SDS) is one of the hottest topics in today’s data center. Naturally, every vendor defines SDS based on their own product range, sometimes leaving customer out of the equation.
Highlights from IBM Analyst Insights 2013
By Torsten Volk on Nov 9, 2016 3:59:25 PM
As every year, IBM invited the analyst community to Stamford, CT, for a deep dialogue on today’s most important topics in enterprise IT. Here is a short overview for everyone interested in IBM’s current world view.
Rapid Evolution – OpenStack Is Growing Up
By Torsten Volk on Nov 9, 2016 3:59:24 PM
The Havana release of OpenStack was launched on October 17, about three weeks prior to the OpenStack Summit in Hong Kong. As always, there are many new features -high availability, load balancing, easier upgrades, plugins for development tools, improved SDN support, fiber channel SAN support, improved bare metal capabilities- and even two new core components, Ceilometer -metering and monitoring- and Heat -orchestration of the creation of entire application environments- to admire. Without any doubt, OpenStack is becoming more enterprise ready with each new release .
War of the Stacks: OpenStack vs. CloudStack vs. vCloud vs. Amazon EC2
By Torsten Volk on Nov 9, 2016 3:59:23 PM
When it comes to cloud technologies, discussions often get passionate or even heated. It’s all about the “war of the stacks”, where much Cool Aid is dispensed to get customers to buy into the respective cult. This discussion reminds me of the old days of enterprise IT, where everything was about technology instead of business value. You either bought one thing or the other and then you were locked in for a half decade. Dark times.
Making Your Service Desk Less Vocal Actually Tells You Things Are as They Should Be
By Dennis Drogseth on Nov 4, 2016 3:03:32 PM
Optimizing the end-user experience has many dimensions to it, and one key element of them is ensuring that any issues from password reset, to application access, to support for multiple endpoints by a single user—are all addressed without your users feeling that they’re queuing up at the Department of Motor Vehicles. This blog leverages EMA research to examine how a truly efficient service desk can make itself all the more effective by becoming more transparent, less verbally visible, and yet ultimately far more end-user empowering.
How to Unleash the Full Value of Hybrid Cloud
By Torsten Volk on Oct 24, 2016 12:26:50 PM
In an ideal world, customers would be able to fully take advantage of the benefits of hybrid cloud by rationally matching infrastructure parameters -cost, performance, reliability, availability, security, regulatory compliance, scalability- with the requirements and dependencies of each application.
The Magnificent Seven ITSM 2.0 Challenges
By Dennis Drogseth on Oct 11, 2016 3:03:31 PM
This is my second blog targeting the next generation of IT service management, or ITSM 2.0. The first blog described the characteristics I see as defining ITSM 2.0. Here we’ll look more closely at the key challenges you might face in getting there from a more traditional ITSM background.
Introducing IT Service Management (ITSM) 2.0: A Cornerstone for Digital and IT Transformation
By Dennis Drogseth on Sep 27, 2016 3:38:11 PM
Over the course of numerous deployment dialogs and multiple research projects starting with last year’s work on “ITSM futures,” I have been tracking a still largely unheralded phenomenon: ITSM teams in many organizations are evolving to take a leadership role in helping all of IT become more efficient, more business aligned, and ever more relevant [...]
The Real Reason Apple Users Are Treated Like Second-Class Citizens
By Steve Brasen on Sep 26, 2016 3:03:15 PM
(With apologies to Jeff Foxworthy) You might be an Apple user if…
The Top 5 IoT Lessons I Learned From Hollywood
By David Monahan on Sep 23, 2016 12:07:46 PM
In my last IoT blog, I talked about the history of IoT and the evolution of issues surrounding IoT devices. In this part of the series, we will expand on the issues around IoT and the data it collects.
Endpoint Management and Security – More Effective as Partners than Adversaries
By Steve Brasen on Sep 2, 2016 10:59:52 AM
The primary function of enterprise IT management is to empower end users with access to technology resources that will boost their productivity and job performance. However, this focus is at odds with the core precepts of IT security which are adopted to minimize the exposure of enterprise systems, applications, and data. I recall that in a number of IT operations management adventures throughout my career, I often joked with colleagues that the most effective way to create a secure environment is to simply shut down all computers in the data center. Naturally, management executives dependent on the IT infrastructure to generate revenue were not amused by my flippancy…and even less happy that their workers had to “jump through hoops” to gain access to IT resources.
Increased Focus on Digital Experience Management Prompts New Research- Done Jointly by Dennis Drogseth and Julie Craig
By Dennis Drogseth on Aug 26, 2016 9:11:12 AM
Digital and user experience management has been the focus of multiple EMA research studies throughout the years, both as a stand-alone topic and as part of EMA’s ongoing examination of critical trends such as digital and operational transformation, IT performance optimization, and of course application performance management (APM). In many respects, optimizing the digital experience [...]
The Enterprise Service Catalog—Unifying IT Services for the Digital Age
By Dennis Drogseth on Aug 26, 2016 9:11:11 AM
While service catalogs are not new, they are becoming increasingly critical to enterprises seeking to optimize IT efficiencies, service delivery and business outcomes. They are also a way of supporting both enterprise and IT services, as well as optimizing IT for cost and value with critical metrics and insights. In this blog we’ll look at [...]
How Is Cloud Changing the Face of IT Service Management?
By Dennis Drogseth on Aug 26, 2016 9:11:11 AM
Cloud is no longer a new topic for IT, or for IT service management (ITSM). But its impact on how ITSM teams work, as well as on how IT works overall, has probably never been greater. Indeed, more and more IT organizations have been “moving to the cloud.” But understanding its relevance can’t be achieved [...]
Effective Security Requires a Change in Mindset and the Protection Paradigm
By David Monahan on Aug 24, 2016 11:05:53 AM
Nearly every day another successful breach is reported. In 2016 alone, organizations from major governmental agencies such as the IRS and Department of Defense, to major retailers including Wendy’s, have succumbed to attack. These organizations are not alone; every major business and governmental sector has been compromised. Large tech companies such as LinkedIn and Oracle, healthcare providers including Premier Healthcare (as well as numerous hospitals), manufacturers, major educational institutions, and large financial organizations have all succumbed to either internal or external threats.
Windows 10…One Year Later
By Steve Brasen on Aug 18, 2016 1:58:29 PM
Time flies when you’re upgrading operating systems. It has officially been a year since Microsoft introduced Windows 10 to much fanfare and approbation. Acceptance of the platform was almost immediate, with many users simply grateful to migrate away from the much-maligned Windows 8 environment. At the core of the problems with the previous edition of Microsoft’s flagship OS was that the GUI was designed to function more effectively on a tablet than on a PC, which infuriated users who had grown used to the Windows 7 look and feel on their laptops and desktops. The release of Windows 10 gave Microsoft’s core audience exactly what it wanted—a unified code base that enables the same applications to be employed on all device architectures (desktops, laptops, tablets, and smartphones) while retaining the look and feel of the classic Windows 7 desktop that they had come to appreciate.
IoT Devices in the Network: Can you find them?
By David Monahan on Aug 10, 2016 2:26:18 PM
In the last year or so, the topic of Internet of Things (IoT) received a lot of attention. Both the concept of the topic and scope of what should be included in IoT changed dramatically in that time. The first commercialization of IoT were wearables such as GoogleGlass. Shortly thereafter came the next wave, with devices such as smart watches. The first security concerns were focused on personal safety due to user distractions, similar to those voiced when smartphones became popular, and then came the invasion of privacy concerns. However, shortly after the first hackers got hold of them and identified attacks to gather data from them. At that point, the view on IoT expanded to recognize that the concept of IoT was actually much broader and had more significant impacts than privacy.
Tips on Getting the Most Out of Your 1:1 iPad Education Program
By Steve Brasen on Jul 5, 2016 8:18:16 AM
There is no greater investment we can make in the future than to prepare our children to successfully navigate the challenges of tomorrow. Of course, predicting the workforce requirements of the future is a bit like trying to capture a fly with a cargo net—just when you think you have it, it slips through the holes and buzzes in a different direction. Nonetheless, it’s safe to assume that workforce mobility will be an essential aspect of the coming generation’s career experiences. Mobile technology is already an integral part of nearly every business role, and its use can only be expected to increase in the years to come. To help support this revolution, Apple has pledged to donate $100 million worth of teaching and learning technology to 114 underserved schools across the country and has offered special discount pricing and volume-purchase programs to all educational institutions. A large number of grade schools have embraced these financial enticements and introduced 1:1 iPad programs that provide every student with their own personal iPad to be used during the duration of a school term.
Q&A from EMA Radar for Workload Automation (WLA): Q1 2016 Webinar
By Dan Twing on May 2, 2016 11:15:13 AM
I recently presented findings from my EMA Radar for Workload Automation (WLA): Q1 2016 report. The recording for the webinar is now live here.
Linux on Power—Poised for Greatness
By Steve Brasen on Apr 22, 2016 11:12:45 AM
For two decades, IBM’s Power Systems family of high-performance servers has been considered the premier alternative to x86-based systems. Combining fast processing, high availability, and rapid scalability, Power Systems are optimized to support big data and cloud architectures. Popularly deployed to run IBM’s AIX and IBM i operating systems, the platform has seen stiff competition in recent years from x86-based Linux systems. In 2013, IBM responded to this challenge by investing a billion dollars into the development of enhancements to the Power line that would support Linux operating systems and open source technologies. This bold move was hailed as a strategy that would greatly improve the attractiveness of the platform and drive broader adoption.
The Desperate Need for Accuracy and Efficiency in Security for Detecting Network Intruders and Other Threat Actors Quickly
By David Monahan on Apr 14, 2016 2:37:49 PM
According to 2015 research reports published by Ponemon, Mandiant, and others, median intruder dwell time in a target network prior to detection ranges from just under to just over 200 days. That is a little over six months and as everyone agrees, totally unacceptable.
5 Reasons to Transition From the Dark Ages to the Digital Age With a Document Management System
By Steve Brasen on Apr 11, 2016 1:18:47 PM
We live in the digital age—or at least many of us do. Today’s IT-savvy users expect to be able to access any data, form, or record from any device at any location and at any time. However, some organizations seem to be perpetually stuck in the dark ages, relying on antiquated paper documents and physical filing cabinets for document retention. Other businesses may have documents in electronic form but lack any method for organizing them beyond just saving them to a basic filesystem. I’ve even known business professionals who store critical records in archive folders in their email package because they lack any other method for document organization. Electronic document management has never been more essential, and organizations that fail to provide adequate document support either will not be able to compete effectively against businesses that do or, even worse, will fail to meet compliance objectives and lose customers due to an inability to provide adequate support services.
Q&A from EMA Radar for Workload Automation (WLA): Q1 2016
By Dan Twing on Mar 16, 2016 8:05:41 AM
Earlier today I presented findings from my recent EMA Radar for Workload Automation (WLA): Q1 2016 report. The recording for the webinar is now live here.
Automation is Key to Staying in the Driver’s Seat of Your Data-driven Strategy
By Dan Twing on Feb 8, 2016 12:54:28 PM
More and more organizations are increasing the use of data in their decision making. EMA describes this as having a data-driven strategy. Recent research has revealed that almost 63% of respondents included data-driven strategies in their organization at a significant level. EMA has been tracking the growth of big data with annual research since 2012. From our 2015 research, you can see in the chart below how organizations are moving forward with their big data projects.




























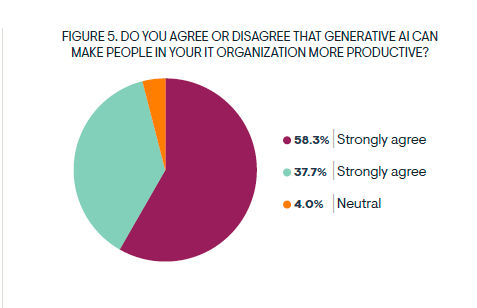






















































%20-%20Copy-1.jpeg)