Nearly every day another successful breach is reported. In 2016 alone, organizations from major governmental agencies such as the IRS and Department of Defense, to major retailers including Wendy’s, have succumbed to attack. These organizations are not alone; every major business and governmental sector has been compromised. Large tech companies such as LinkedIn and Oracle, healthcare providers including Premier Healthcare (as well as numerous hospitals), manufacturers, major educational institutions, and large financial organizations have all succumbed to either internal or external threats.
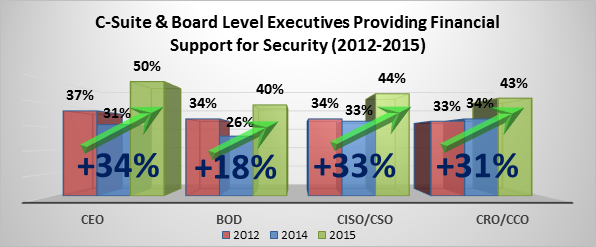
Effective Security Requires a Change in Mindset and the Protection Paradigm
By David Monahan on Aug 24, 2016 11:05:53 AM
IoT Devices in the Network: Can you find them?
By David Monahan on Aug 10, 2016 2:26:18 PM
In the last year or so, the topic of Internet of Things (IoT) received a lot of attention. Both the concept of the topic and scope of what should be included in IoT changed dramatically in that time. The first commercialization of IoT were wearables such as GoogleGlass. Shortly thereafter came the next wave, with devices such as smart watches. The first security concerns were focused on personal safety due to user distractions, similar to those voiced when smartphones became popular, and then came the invasion of privacy concerns. However, shortly after the first hackers got hold of them and identified attacks to gather data from them. At that point, the view on IoT expanded to recognize that the concept of IoT was actually much broader and had more significant impacts than privacy.
The Desperate Need for Accuracy and Efficiency in Security for Detecting Network Intruders and Other Threat Actors Quickly
By David Monahan on Apr 14, 2016 2:37:49 PM
According to 2015 research reports published by Ponemon, Mandiant, and others, median intruder dwell time in a target network prior to detection ranges from just under to just over 200 days. That is a little over six months and as everyone agrees, totally unacceptable.
HEAT Software Meets the Need for Endpoint Protection Head-On
By David Monahan on Dec 11, 2015 12:40:49 PM
In many organizations, endpoints see virtually constant change. Users access, download, and utilize applications, data, drivers, files, toolbars, widgets, etc., introducing both new security threats and undocumented changes in systems and processes. For better or for worse, all of these activities leave their mark on the endpoint.
The Rise of Thingbots in the Internet of Things (IoT)
By David Monahan on Nov 20, 2015 12:50:39 PM
The Internet can be a pretty scary place. Places like the dark web exist in the form of trading houses with stolen personal information from credit cards and social security numbers, to health records and full identities being obtained for a price. Malware development and deployment and other attack services such as DDoS and botnets can be rented by the hour. Recent reports indicate that DDoS attacks are increasing in both frequency and size, and the problem of botnets being used as attack networks or launch points in DDoS and other malicious activities is significant. Indications are that it will only continue to get worse.
EMA Research Shows that Cyber Security is Achieving Executive Visibility in a Big Way
By David Monahan on Nov 20, 2015 12:50:32 PM
One of the services that EMA provides to the tech industry is research. During the course of the year, numerous projects are launched to help IT consumers and vendors understand market perceptions. EMA then provides analysis and forecasts on trends based upon those perceptions.
The Limits of Packet Capture
By David Monahan on Aug 19, 2015 3:42:12 PM
In preparation for my new ‘Achieving Hi-Fidelity Security’ research project, I thought I would post a relevant blog I wrote for InformationSecurityBuzz.com.
Vectra Provides Pervasive Visibility & Analysis to Detect Cyber Attacks
By David Monahan on Apr 9, 2015 2:21:39 PM
Though cyber attacks have been around for years, in 2014 there was an explosion in the volume of attacks and a marked increase in the losses and damages they inflicted. In 2015, this does not seem to be lightening up.
Leveraging User Activity Monitoring to Protect Information and Employees from Cyber Threats
By David Monahan on Mar 4, 2015 2:46:04 PM
Historically, many organizations and personnel have been concerned about user activity monitoring (UAM). Certain business cultures feel that these activities are an invasion of privacy or are distrustful. However, in today’s Internet connected, data driven world, having specific information or data means the difference in being a market leader and being out of business.
PFP CyberSecurity Breaks on to the Scene to Identify Malware at the Chip Level.
By David Monahan on Mar 2, 2015 11:51:59 AM
A few weeks ago, I briefed with a new company called PFP Cybersecurity, also known as Power Fingerprinting, Inc., and was so intrigued by the concept alone that I wrote a Vendor to Watch about them. They officially launched on January 26, , and currently their claim to fame is their physics-based scanning technology which monitors the electromagnetic frequency (EMF) emanations of a microchip while operating. It then compares those readings to either a previous reading or to an established manufacturer’s baseline to determine the state of the chip. There are numerous uses for the technology from supply chain chip counterfeit detection, to operational failure prediction, and most unique of all, malware detection. The scanners are useful in many environments, but especially those that are change and failure/fault intolerant like space vehicles, nuclear and other critical infrastructure environments, and multiple military and natural resource acquisitions environments because they are touchless. There is nothing to install on the system using the microchip, so no change control requests or outage windows are needed. The other interesting thing about their technology is it is disruptive to the current scanner market, costing significantly less than competing products. Their platform is that each model of chip has a different EMF/power signature. These also vary by manufacturer because of variances in raw materials sourcing and manufacturing processes. It is well known that under use conditions, especially when heat dissipation is not well implemented, the chips degrade over time until failure. (That’s the point when the ‘magic smoke’ comes out and it stops working.) The cool part for me was the concept of malware detection. Aside from the physical properties of the chip, the software running on the chip will change the output pattern because of register changes and associated changes in code execution. This means that if a probe is scanning a chip and malware installs itself, the scanner can detect it at the time of installation and alert an operator that it has happened, potentially avoiding larger impact failures and data exfiltration. This technique reminds me of classic side channel attacks on CPUs that perform encryption to attempt a key extraction based on how the various chip leads changed over time. (The key difference being those attacks required contact with the open leads.) In a sense, this technology is highly disruptive, in a positive way, to both the current scanning system suppliers because of the lower cost, and to the infrastructure and supply chains because of not only the cost, but also because of the reported accuracy. It will significantly improve supply chain verification, system reliability, and security. I am looking forward to see how they progress in the marketplace over the next few years. About PFP Cybersecurity Headquartered in Washington, D.C., PFP Cybersecurity provides a unique, anomaly-based cyber security threat detection technology that can instantly identify software and hardware intrusion including active and dormant attacks. With its innovative technology, PFP shortens the compromise detection gap to milliseconds by monitoring changes in electromagnetic frequencies and power usage. This physics-based technology can be applied to detect advanced malware and sophisticated threats in critical cyber systems. It can also detect hardware Trojans and counterfeits in the supply chain. For more information, please visit: www.pfpcyber.com