One of the services that EMA provides to the tech industry is research. During the course of the year, numerous projects are launched to help IT consumers and vendors understand market perceptions. EMA then provides analysis and forecasts on trends based upon those perceptions.
David Monahan

Recent Posts
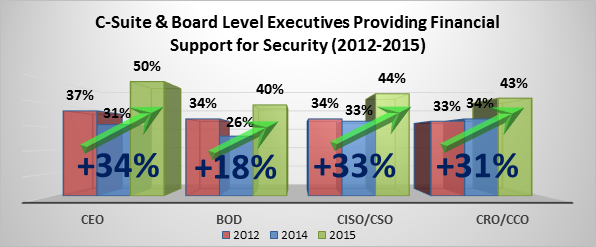
EMA Research Shows that Cyber Security is Achieving Executive Visibility in a Big Way
By David Monahan on Nov 20, 2015 12:50:32 PM
The Limits of Packet Capture
By David Monahan on Aug 19, 2015 3:42:12 PM
In preparation for my new ‘Achieving Hi-Fidelity Security’ research project, I thought I would post a relevant blog I wrote for InformationSecurityBuzz.com.
Vectra Provides Pervasive Visibility & Analysis to Detect Cyber Attacks
By David Monahan on Apr 9, 2015 2:21:39 PM
Though cyber attacks have been around for years, in 2014 there was an explosion in the volume of attacks and a marked increase in the losses and damages they inflicted. In 2015, this does not seem to be lightening up.
Leveraging User Activity Monitoring to Protect Information and Employees from Cyber Threats
By David Monahan on Mar 4, 2015 2:46:04 PM
Historically, many organizations and personnel have been concerned about user activity monitoring (UAM). Certain business cultures feel that these activities are an invasion of privacy or are distrustful. However, in today’s Internet connected, data driven world, having specific information or data means the difference in being a market leader and being out of business.
PFP CyberSecurity Breaks on to the Scene to Identify Malware at the Chip Level.
By David Monahan on Mar 2, 2015 11:51:59 AM
A few weeks ago, I briefed with a new company called PFP Cybersecurity, also known as Power Fingerprinting, Inc., and was so intrigued by the concept alone that I wrote a Vendor to Watch about them. They officially launched on January 26, , and currently their claim to fame is their physics-based scanning technology which monitors the electromagnetic frequency (EMF) emanations of a microchip while operating. It then compares those readings to either a previous reading or to an established manufacturer’s baseline to determine the state of the chip. There are numerous uses for the technology from supply chain chip counterfeit detection, to operational failure prediction, and most unique of all, malware detection. The scanners are useful in many environments, but especially those that are change and failure/fault intolerant like space vehicles, nuclear and other critical infrastructure environments, and multiple military and natural resource acquisitions environments because they are touchless. There is nothing to install on the system using the microchip, so no change control requests or outage windows are needed. The other interesting thing about their technology is it is disruptive to the current scanner market, costing significantly less than competing products. Their platform is that each model of chip has a different EMF/power signature. These also vary by manufacturer because of variances in raw materials sourcing and manufacturing processes. It is well known that under use conditions, especially when heat dissipation is not well implemented, the chips degrade over time until failure. (That’s the point when the ‘magic smoke’ comes out and it stops working.) The cool part for me was the concept of malware detection. Aside from the physical properties of the chip, the software running on the chip will change the output pattern because of register changes and associated changes in code execution. This means that if a probe is scanning a chip and malware installs itself, the scanner can detect it at the time of installation and alert an operator that it has happened, potentially avoiding larger impact failures and data exfiltration. This technique reminds me of classic side channel attacks on CPUs that perform encryption to attempt a key extraction based on how the various chip leads changed over time. (The key difference being those attacks required contact with the open leads.) In a sense, this technology is highly disruptive, in a positive way, to both the current scanning system suppliers because of the lower cost, and to the infrastructure and supply chains because of not only the cost, but also because of the reported accuracy. It will significantly improve supply chain verification, system reliability, and security. I am looking forward to see how they progress in the marketplace over the next few years. About PFP Cybersecurity Headquartered in Washington, D.C., PFP Cybersecurity provides a unique, anomaly-based cyber security threat detection technology that can instantly identify software and hardware intrusion including active and dormant attacks. With its innovative technology, PFP shortens the compromise detection gap to milliseconds by monitoring changes in electromagnetic frequencies and power usage. This physics-based technology can be applied to detect advanced malware and sophisticated threats in critical cyber systems. It can also detect hardware Trojans and counterfeits in the supply chain. For more information, please visit: www.pfpcyber.com
Leveraging Security Policy Orchestration to “Bake Security in” to SDDC Environments
By David Monahan on Jan 27, 2015 9:50:24 AM
I have a new guest blog just posted at for Tufin around Security Policy Orchestration. You can check it out here.
Breach Detection, Sony Entertainment and Vectra Networks…
By David Monahan on Dec 19, 2014 1:25:56 PM
Working in information security for the past 20 years, I have seen a lot. Though there have been many multi-million dollar impact breaches, the recent Sony Pictures hack and subsequent data exposure and extortion is probably the most impactful to a company out of the previous breaches this year.
Allgress Insight Risk Management Suite Brings Flexibility and Functionality to IT-GRC
By David Monahan on Dec 19, 2014 1:04:02 PM
When I started out in security, only very large organizations with a mature set of business processes dared to talk about implementing some form of governance, risk, and compliance (GRC) or enterprise program (e-GRC). They generally did it in an attempt to get ISO or similar certification, or to “move their programs to the next level,” and some, I think, attempted it just to prove they did it. Many of those efforts were monumental, costing millions of dollars and taking years to complete. However, a significant number seemed to end in compromise, yielding a smaller end result or totally failing after thousands of man hours and millions of dollars for software, systems, and consulting had been spent.
Is EMV an Expensive Security Misstep for the Payments Industry?
By David Monahan on Dec 8, 2014 10:04:28 AM
There is no disagreement that the current mag-stripe technology used in the USA and other countries outside of the EU is antiquated and lends itself to fraud. The data is easily copied using various methods from manual card data copying and shoulder surfing, to database compromise and POS terminal malware. Cards can be reproduced with off-the-shelf plastic blanks and a simple machine you can buy on the Internet.
Cloud Security Alliance Hack-A-Thon and the Software Defined Perimeter
By David Monahan on Nov 7, 2014 11:00:31 AM
The Cloud Security Alliance (CSA) is a not-for-profit think tank of volunteers that spend their time trying to better the internet. These people are the antithesis of cybercriminals; they spend their energy trying to figure out ways to make our data safer. They create best practices for providing security assurance within cloud computing, or in this case, they determine how a cloud environment can be used to enhance and scale authentication for a service that can be cloud-based or private data center-based.