The Internet can be a pretty scary place. Places like the dark web exist in the form of trading houses with stolen personal information from credit cards and social security numbers, to health records and full identities being obtained for a price. Malware development and deployment and other attack services such as DDoS and botnets can be rented by the hour. Recent reports indicate that DDoS attacks are increasing in both frequency and size, and the problem of botnets being used as attack networks or launch points in DDoS and other malicious activities is significant. Indications are that it will only continue to get worse.
The Rise of Thingbots in the Internet of Things (IoT)
By David Monahan on Nov 20, 2015 12:50:39 PM
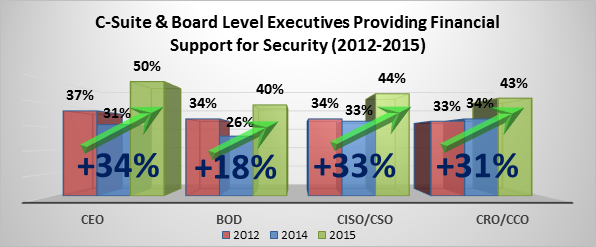
EMA Research Shows that Cyber Security is Achieving Executive Visibility in a Big Way
By David Monahan on Nov 20, 2015 12:50:32 PM
One of the services that EMA provides to the tech industry is research. During the course of the year, numerous projects are launched to help IT consumers and vendors understand market perceptions. EMA then provides analysis and forecasts on trends based upon those perceptions.
Why Analytics and Automation Are Central to ITSM Transformation
By Dennis Drogseth on Nov 9, 2015 11:12:00 AM
In research done earlier this year, we looked at changing patterns of IT service management (ITSM) adoption across a population of 270 respondents in North America and Europe. One of the standout themes that emerged from our findings was the need for the service desk to become a more automated and analytically empowered center of [...]
Digital Transformation and the New War Room
By Dennis Drogseth on Nov 3, 2015 10:42:46 AM
In August EMA surveyed 306 respondents in North America, England, France, Germany, Australia, China and India about digital and IT transformation. The goal was in part to create a heat map around just what digital and IT transformation were in the minds of both IT and business stakeholders. We targeted mostly leadership roles, but also [...]
User Experience Matters in Self-Service Provisioning
By Steve Brasen on Oct 26, 2015 12:08:22 PM
If you’re like me, you are increasingly becoming reliant on online shopping to replace the more arduous task of physical in-store shopping. I find this is particularly true during the holiday season when the idea of fighting traffic and elbowing crowds to desperately search numerous shops in order to find just the right gift for Aunt Phillis (who’s just going to hate whatever she receives anyway) gives way to the more idyllic setting of web-surfing multiple stores simultaneously from the privacy of your home while the dulcet tones of Nat King Cole playing gently in the background lull you into the holiday spirit (a little spiced eggnog on the side doesn’t hurt either). But have you ever stopped to consider why you shop at some websites and not at others? Certainly item prices have something to do with it, as does the breadth of product selection. However, there is almost certainly a third element involved—one of which you may not even be consciously aware: The quality of the online store shopping experience directly impacts the likelihood that you (and other consumers) will purchase items on it. Websites that are friendly, professional, and easy to use are far more likely to produce sales than those that are confusing and difficult to navigate.
Top 5 Reasons IT Administrators Are Working Too Hard Managing Endpoints
By Steve Brasen on Oct 9, 2015 10:25:18 AM
IT administration is a thankless job. Let’s face it—the only time admins gain any recognition is when something goes wrong. In fact, the most successful IT administrators proactively manage very stable environments where very few failures and performance degradations occur. Unfortunately, though, this is rarely the case, and it is far more common for admins to get stuck in the break/fix cycle of reactive “firefighting” where problems are never truly resolved and are destined to occur again. Making matters worse, increasing requirements for mobility, business agility, high performance, and high availability have substantially increased IT administrator workloads. With this kind of pressure, it’s no wonder IT professionals are frustrated.
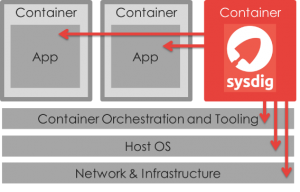
Running Containers Doesn’t Have To Mean Running Blind
By Dan Twing on Oct 6, 2015 2:17:15 PM
The idea of containers has been around for a long time in various forms on various operating systems. It has been part of the Linux kernel since version 2.6.24 was released in 2008. However, containers did not become mainstream until a couple years ago when Docker was first released in March 2013. Docker introduced container management tools and a packaging format, which made container technologies accessible to developers without Linux kernel expertise. By doing so Docker led the way to making containers mainstream as well as one of the hottest trends in application development and deployment because it simplified the way applications are packaged. While this has big advantages, containers are still early in their lifecycle and lack operational maturity. The ease of use with which Docker images can be created leads to image sprawl, previously seen with VMs, and exacerbates the problem of managing security and compliance of these images. Container environments do not integrate well to existing developer tools, complicating team development due to a lack of staging and versioning for preproduction and production promotion. Also, containers do not integrate with existing monitoring tools, complicating management. However, new tools are being developed targeting Docker as an application delivery format and execution environment by an ever-growing Docker community. Many of the benefits are on the development side of the house, with the promise of DevOps benefits. Running in production can be a different story.
Are Laptops Really Mobile Devices?
By Steve Brasen on Sep 25, 2015 10:39:16 AM
When people think of IT mobility, the images most immediately conjured regard smartphones and tablets. In truth, however the mobile device landscape could be considered broader than this. The basic definition of a mobile device is simply “any computing device designed principally for portability.” By that definition, laptops should clearly be included in that scope. However, some definitions state that a mobile device must be “handheld” indicating size is a factor without actually specifying how small a device must be to achieve that designation. Regardless of size limitations, those definitions still favor inclusion of laptops since many are available with a form facture that is smaller than some of the larger tablets. Therefore, the defining descriptor for a mobile device must fall to its portability, which also happens to be the key differentiator between a laptop and a desktop PC. Logically, therefor, a laptop is, in fact, a mobile device.
Process, Dialog, and Workflow: A Formula for Interconnection and Automation
By Dennis Drogseth on Sep 24, 2015 11:42:46 AM
As a follow-up to my previous columns on change management, I’d like to step back a little and shine a light on an even broader landscape. Here I’ll touch briefly on process, dialog, and workflow as a triad that can help IT organizations move forward toward a more efficient and potentially more business-aligned way of [...]
Why It’s Never Too Soon to Think about IPv6 Network Management
By Shamus McGillicuddy on Sep 9, 2015 3:23:37 PM
Most network managers are still many years away from turning on Internet Protocol version 6 (IPv6) in their enterprise local area networks (LANs). Private non-routable IPv4 address ranges can happily exist behind a network address translation (NAT) gateway for the foreseeable future. However, things could change. At any time, someone above your pay grade might [...]