I recently presented findings from my EMA Radar for Workload Automation (WLA): Q1 2016 report. The recording for the webinar is now live here.
Q&A from EMA Radar for Workload Automation (WLA): Q1 2016 Webinar
By Dan Twing on May 2, 2016 11:15:13 AM
Linux on Power—Poised for Greatness
By Steve Brasen on Apr 22, 2016 11:12:45 AM
For two decades, IBM’s Power Systems family of high-performance servers has been considered the premier alternative to x86-based systems. Combining fast processing, high availability, and rapid scalability, Power Systems are optimized to support big data and cloud architectures. Popularly deployed to run IBM’s AIX and IBM i operating systems, the platform has seen stiff competition in recent years from x86-based Linux systems. In 2013, IBM responded to this challenge by investing a billion dollars into the development of enhancements to the Power line that would support Linux operating systems and open source technologies. This bold move was hailed as a strategy that would greatly improve the attractiveness of the platform and drive broader adoption.
The Desperate Need for Accuracy and Efficiency in Security for Detecting Network Intruders and Other Threat Actors Quickly
By David Monahan on Apr 14, 2016 2:37:49 PM
According to 2015 research reports published by Ponemon, Mandiant, and others, median intruder dwell time in a target network prior to detection ranges from just under to just over 200 days. That is a little over six months and as everyone agrees, totally unacceptable.
5 Reasons to Transition From the Dark Ages to the Digital Age With a Document Management System
By Steve Brasen on Apr 11, 2016 1:18:47 PM
We live in the digital age—or at least many of us do. Today’s IT-savvy users expect to be able to access any data, form, or record from any device at any location and at any time. However, some organizations seem to be perpetually stuck in the dark ages, relying on antiquated paper documents and physical filing cabinets for document retention. Other businesses may have documents in electronic form but lack any method for organizing them beyond just saving them to a basic filesystem. I’ve even known business professionals who store critical records in archive folders in their email package because they lack any other method for document organization. Electronic document management has never been more essential, and organizations that fail to provide adequate document support either will not be able to compete effectively against businesses that do or, even worse, will fail to meet compliance objectives and lose customers due to an inability to provide adequate support services.
Q&A from EMA Radar for Workload Automation (WLA): Q1 2016
By Dan Twing on Mar 16, 2016 8:05:41 AM
Earlier today I presented findings from my recent EMA Radar for Workload Automation (WLA): Q1 2016 report. The recording for the webinar is now live here.
Automation is Key to Staying in the Driver’s Seat of Your Data-driven Strategy
By Dan Twing on Feb 8, 2016 12:54:28 PM
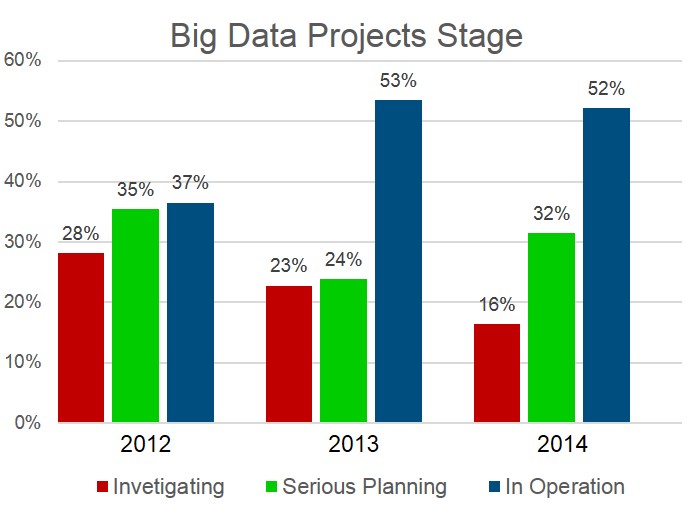
More and more organizations are increasing the use of data in their decision making. EMA describes this as having a data-driven strategy. Recent research has revealed that almost 63% of respondents included data-driven strategies in their organization at a significant level. EMA has been tracking the growth of big data with annual research since 2012. From our 2015 research, you can see in the chart below how organizations are moving forward with their big data projects.
2016: Looking Ahead at ITSM—Want to Place Any Bets?
By Dennis Drogseth on Jan 22, 2016 12:52:29 PM
I thought I’d begin the year by making some predictions about what to look for in 2016 in the area of IT service management (ITSM). For those of you who have been following my blogs with any regularity, and particularly for those who sat in on our webinar for the research report “What Is the [...]
Who Owns User and Customer Experience Management?
By Dennis Drogseth on Jan 22, 2016 12:52:28 PM
There is growing industry attention to user, customer, and digital experience management—often condensed by the acronym UEM for “user experience management.” This attention is more than justified, but most of the buzz leaves out critical questions like, “What is user experience management?”, “Who really runs (or who should run) the UEM show in the digital [...]
HEAT Software Meets the Need for Endpoint Protection Head-On
By David Monahan on Dec 11, 2015 12:40:49 PM
In many organizations, endpoints see virtually constant change. Users access, download, and utilize applications, data, drivers, files, toolbars, widgets, etc., introducing both new security threats and undocumented changes in systems and processes. For better or for worse, all of these activities leave their mark on the endpoint.
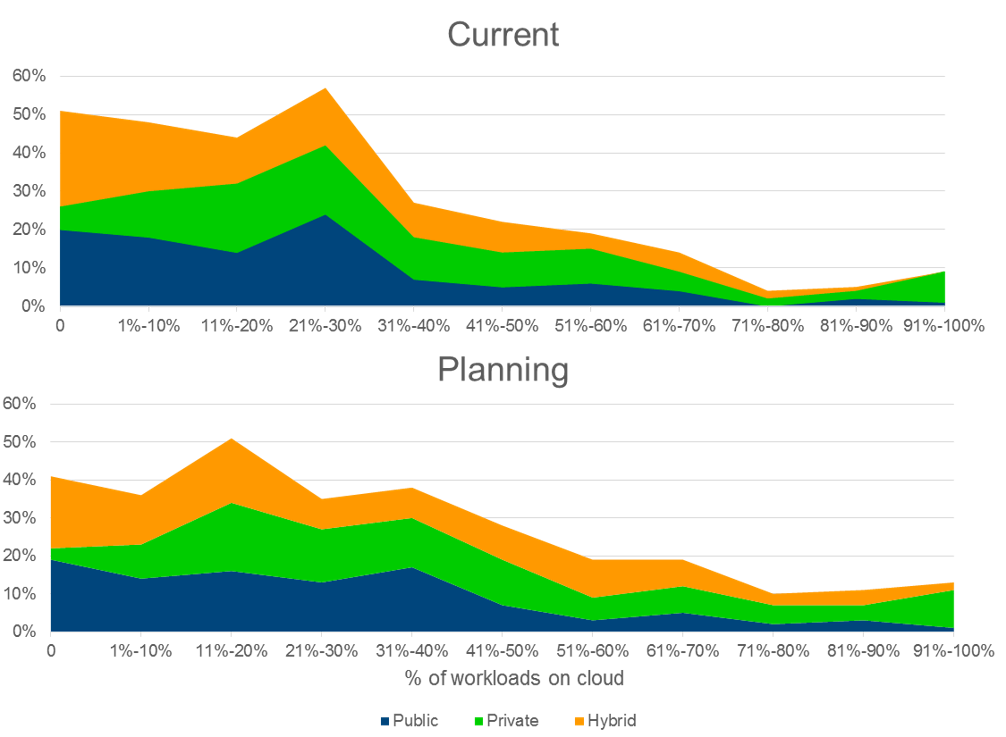
Best Practices for Innovating Through Cloud Technologies – Utilizing Public, Private, and Hybrid Cloud
By Dan Twing on Nov 25, 2015 9:15:12 AM
Cloud computing can speed up deployment, reduce costs, and increase efficiency and connectivity. It can open up new ways to get computing work done, but more importantly, the inherent connectivity can change the way employees interact with each other and with customers. It can also change the way companies interact with suppliers and partners. The ease of standing up new apps and connecting with users through mobile devices, as well as the minimal capital investment, can spur innovation.